Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Reviews
Hasib Anwar
- on January 06, 2020
Why Hyperledger Indy Is Important For Digital Identities?
Hyperledger Indy can give you back the control over your own identity and data. Feeling intrigued? Let’s dissect the platform from the very core to understand how this project operates.
With the evolution of the digital world, all of us want to stay online all the time. However, while performing various tasks, you may have to disclose your personal information on multiple platforms as well. Especially when you are shopping online, you need to give them your financial information to purchase anything.
And that’s why the need for digital identities is more than ever. Well, no matter how secured the online platforms claim to be, there seems to be an overwhelming number of identity thefts in every case.
From the moment you disclose your personal information, it gets stored in multiple databases. And these databases aren’t secured from hackers. More so, platforms now use our data without our consent. Additionally, these platforms also sell your information to advertisement clients.
This definitely doesn’t feel like you are in control, are you? And this is where Hyperledger Indy comes to play.
Excited to learn the basic and advanced concepts of Hyperledger Fabric? Enroll Now in Getting Started with Hyperledger Fabric Course
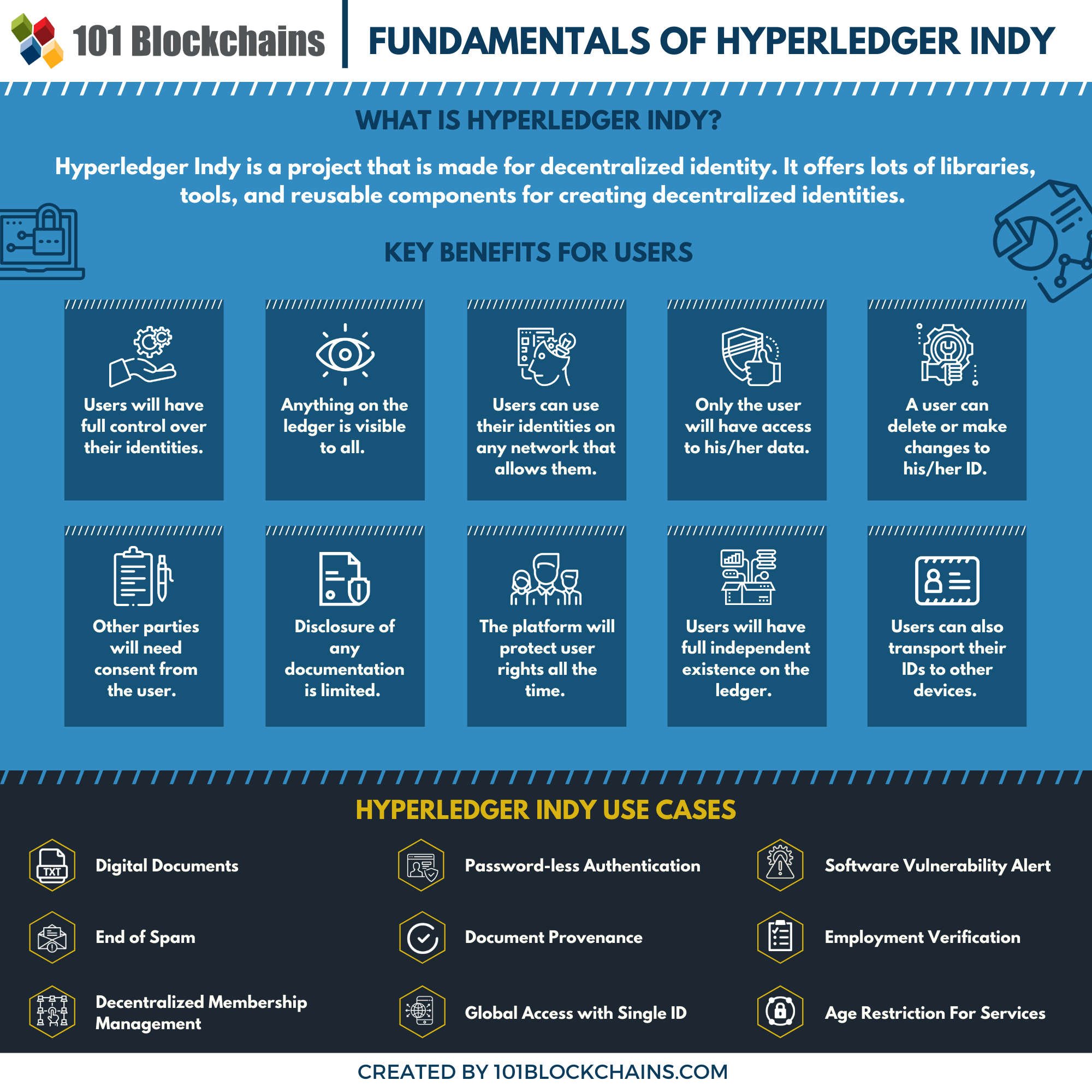
What Is Hyperledger Indy?
Hyperledger Indy is a project under the umbrella project Hyperledger blockchain backed by the Linux Foundation. It’s mainly a framework made for decentralized identity and also a distributed ledger. In reality, with Hyperledger Indy architecture, you can create digital identities that would be rooted in the blockchain or any other form of distrusted ledger.
Additionally, with Hyperledger Indy architecture, you’ll get lots of libraries, tools, reusable components, and many more.
More so, the best part is that every identity coming out of this Hyperledger Indy architecture is interoperable across multiple domains, organizational silos, and applications.
Thus, it means that you can solely rely on a shared truth along with all your associates.
Anyhow, with the Hyperledger Indy tutorial, you can now ask questions like who you are dealing with and how you can verify your information before interacting with any other party. As it offers a transparent approach, there would be nothing hidden from you.
In reality, Hyperledger Indy vs. Fabric is a completely different kind of topic. Although they may seem like similar projects, in reality, they are not. Fabric is more suited for a wide-ranging of use cases and industries. On the other hand, Indy is specifically created for self-sovereign identity management. So, any industry dealing with identity management can use it.
So, if we do a Hyperledger Indy vs. Fabric comparison, you’ll find that both of the projects have something different to offer to the table.
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2020/01/Hyperledger-Indy.png' alt='Hyperledger Indy='0' /> </a>
Key Features of Hyperledger Indy
From the Hyperledger Indy tutorial, you can learn about the key features of this platform. Let’s see what they are –
-
Self-sovereignty
From Hyperledger Indy documentation, you’ll know that the framework stored identities on a distributed ledger. There are special artifacts that the platform will store for you. Basically, these artifacts will include cryptographic accumulators, proof of existence, public keys, and many more.
No one, but you can only change or remove your identity from it.
-
Privacy
By default, the platform will preserve all your privacy. In reality, the Hyperledger Indy documentation outlines how it will preserve the privacy settings and how it can operate without any contradiction with any party.
More so, you’ll also know just how it can provide security in a decentralized system.
-
Verifiable claims
In reality, the identity claims may have similar credentials, such as in driver’s license or birth certification or in the passport. But you can combine these to make it even more powerful.
More so, you can prove your identity with one single ID from the ledger—no need to submit all the documentation in every case anymore.
-
Purpose-built
It’s purpose-built for decentralized identities only. According to the Hyperledger Indy documentation, you use the platform ready for integration in any company that deals with identities. So, you won’t have to go for any other solution or come up with your own platform solely to incorporate in your industries.
Want to know what a distributed ledger technology is? Learn more about it from our distributed ledger technology guide now!
-
Identity Correlation-resistant
This is the best part of Hyperledger Indy. According to the Hyperledger Indy documentation, it’s completely identity correlation-resistant. So, you won’t have to worry about leaving any breadcrumbs from one ID to another.
More so, there’s no way the platform will connect two IDs or have two similar identifications in the ledger.
-
Decentralized Identifiers (DIDs)
According to the Hyperledger Indy documentation, all the decentralized identifiers are globally resolvable and unique without needing any central party in the mix.
So, every decentralized identity on the platform will have a unique identifier that will solely belong to you.
No one can claim or even use your identity as your own. So, the identity theft issue would reduce greatly.
-
Peer-to-peer Connection
According to the Hyperledger Indy tutorial, the platform has a peer-to-peer connection. So, any communication would happen between two peers. In reality, it’s different from any other centralized servers because, in those, the server would act as the middleman.
But in Hyperledger Indy, there won’t be a middleman.
-
Zero-Knowledge Proofs
With help from zero-knowledge proof, you can disclose only the information needed without anything else. So, when you have to prove your credentials, you can only choose to release the information that you need. For example, if you need to disclose your birth certificate, then you can choose only to do that.
So, this gives you an additional amount of control over your information.
Curious to learn about the value advantages of ZKPs for blockchain security? Enroll Now in Zero Knowledge Proofs (ZKP) Masterclass Course
Why Do You Need Hyperledger Indy?
Let’s explore some of the main issues of existing infrastructure. This will help you understand why this project is really important.
-
Centralized Identity Management
First of all, let’s check out what centralized Identity management has been doing for all these years. In reality, the Internet was built to connect people without relying on an intermediary. However, as the internet started to become more privatized, third-party intermediaries began to emerge.
And at last, now it became a fundamental part of this infrastructure. Anyhow, the foundation is based on a centralized model that comes with a sole controlling entity that has access to everything.
In reality, the centralized authority can make changes to your content, can steal your information, and even misuse it any way they please.
More so, even if they don’t steal it, they still collect a massive amount of personal information that hackers can get easily. Additionally, the huge volume of information also increased the chances of data breaches.
That’s why these centralized identity management system fails horribly and can lead to these issues –
-
Lack of Transparency
As there is no transparency in centralized systems, there seem to a lot of privacy violation issues rising over the years. For example, DeepMind’s illegal patient data sharing, Cambridge Analytica Scandal, and fining Facebook for stealing user information for ads.
All these sources didn’t confirm whether the user had consent or not. More so, they didn’t follow any privacy rules and tracked all their history to produce ads.
-
Lack of Control
Another major flaw of the centralized system is that you don’t have any control over it. In many cases, your information will be used according to the authorities’ needs. For example, even if you delete your Facebook account, Facebook will still have some information left on the server.
So, you can never delete all of the information from them. Anyhow, this is just one of the bad consequences that come with a centralized server model.
-
Identity Theft
Any hacker can easily hack all your data that you shared on the internet without breaking a sweat. More so, the issue comes when someone hijacks your data and they demand a high ransom for it to get back.
It can be any type of information such as your bank account information, your company’s sensitive data, or even your personal files that you don’t want out in the open.
According to the Breach Level Index, every second, 214 records are stolen or gets lost. So, it means that in a day, 18,525,816 records get stolen every single day! Even your data can be on that list, and you won’t even know about it.
As you can see, with this much data hacks happening every day, it’s evident that centralized systems are failing hard to protect the information from the hackers.
Build your identity as a certified Web3 & Blockchain expert with 101 Blockchains’ Web3 & Blockchain Certifications designed to provide enhanced career prospects.
-
No Global Identity
The centralized systems don’t have any global record system, which can hinder when applying for certain documents such as passport, driving license, PAN card, etc. So, you have to submit the same documents every time you apply for these.
In reality, it can be really time-consuming and makes the process cumbersome. At present, there isn’t any global authority that can authenticate your documents with only a single ID.
As a result, getting these documents can become really hard when you go from one country to another. More so, the process of collecting all this information is tedious work.
-
Economic Burden
The identity management system currently covers their major stakeholders – identity holders, verifying companies, and parties that verify the users. Overall, the payment for each sector costs a hefty amount of money.
Anyhow, KYC companies have to process information from a lot of organizations such as insurance companies, hospitals, banks, etc. that makes it overburdened and would need more resources.
To fulfill all the demands of manpower, the companies charge a high verification cost, and that becomes a hidden processing fee for individuals.
As you can see, in the end, you will be the one paying more to verify your credentials. According to a survey, KYC companies spend over $48 million every year just for the verification process.
More so, the time to clear an individual is 26 days, and also, if the user wants to make any changes, it takes 20 days to do it, which is a lot of time.
Therefore, it does become a burden to all stakeholders in the long run. Anyhow, the federal identities could use a single identity for many purposes with the user’s consent. However, as it’s stored in a centralized server, it too becomes non-transparent to the users.
-
User-Centric Identity
Thus, after all the models failed, the focus shifted towards a more user-centric identity where users will control what information is shared. But it was also limited to identity register that can revoke access anytime they want.
Thus, the concept of Self-sovereign identities started to rise, and it will keep the information in the user’s hand rather than in organizations or third-parties. But the base of the architecture needs a decentralized platform.
And this is where Hyperledger Indy architecture comes into play. As it’s a decentralized platform, it can be the perfect solution to all of the issues. More so, the Hyperledger Indy architecture is specifically for identity-based solutions.
What Are the Typical Components of Hyperledger Indy?
-
Cryptography
Any kind of identity solution that will use the Hyperledger Indy agent will use zero-knowledge cryptography. In this Hyperledger Indy SDK, a zero-knowledge proof will ensure that one user can prove to any other user that they know certain information without revealing anything else.
So, it means that the user will only share that he/she knows certain information, and based on that, the user can know whether he/she is telling the truth or not.
-
Nodes
In Hyperledger Indy SDK, all the nodes can be classified into three major types – full node, a master node, and nodes. In reality, a device that performs transactions on the blockchain is a node. On the other hand, in Hyperledger Indy SDK, a client that operates on the network and maintains a full copy of the ledger is a full node.
Anyhow, a master node is actually responsible for decentralized governance in the Hyperledger Indy SDK.
But what about Hyperledger Indy consensus? Well, in reality, Hyperledger Indy consensus is actually Redundant Byzantine Fault Tolerance (RBFT) protocols.
More so, the Hyperledger Indy consensus is actually an advanced form of the Plenum Byzantine Fault Tolerance model.
In this Hyperledger Indy consensus, you will see multiple parallel instances of BFT (Byzantine Fault Tolerance) protocol. More so, every instance will have a primary replica. Even though all other protocol instances can order a request, still only a master instance can execute them.
That’s why Hyperledger Indy consensus is actually quite efficient.
-
Ledger
According to the Hyperledger Indy tutorial, the Merkle tree backs up the ledger. More so, all the nodes have replicas of the ledger.
-
Agent
Hyperledger Indy agents can come in many varieties. In reality, some of them may be quite simple and static. And these are more suited for IoT use cases that require a single hard-wired connection. On the other hand, Hyperledger Indy agents are also cloud-based and complex. These are more suited for enterprise use cases.
-
State and Storage
It’s kind of similar to Ethereum, and the state of the network is maintained by Patricia Trie. Basically, it’s a combination of Merkle Trie and Radix Trie. On the other hand, storage in the system is implemented with leveldb as it offers implementation of value/key database. It also offers ordered mapping.
Start your blockchain journey Now with the Enterprise Blockchains Fundamentals!
User Benefits of Hyperledger Indy
Control: Users will have full control over their identities.
Transparency: Anything on the ledger is visible to all. However, the information will be encrypted.
Access: Only the user will have access to his/her data.
Interoperability: Users can use their identities on any network that allows them.
Consent: Any other party that wants to access certain information will need consent from the user.
Existence: All the users will have full independent existence on the ledger.
Longevity: It will stay on the ledger as long as a user wants. So, they can also delete their identities if they want.
Portability: Users can also transport their IDs to other devices.
Minimization: Disclosure of any kind of documentation comes with heavy minimization.
Protection: The platform will protect user rights all the time.
Self-Sovereign Identity Players in Hyperledger Indy
There are specifically three types of identity players in Hyperledger Indy. Let’s see what these are –
Identity Provider: It doesn’t have any centralized provider but works in a decentralized manner with pre-defined rules. Basically, these nodes will issue their identities.
Identity Owner: Identity Owners have their verified identities in the ledger and will have public-private key pairs for security.
Identity Validator: These nodes have gained trust in the network and take part in the validation process.
How Does the Process Work?
A user can provide their name or any other human-memorable form for the ID in the initial phase.
After that, the ID name will be converted into a unique code or key, which is called decentralized Identifiers (DID) in the ledger. There would be a value associated with it known as the DID descriptor object (DDO). Together they are called DID records.
You can identify a user with the help of a DID record. In reality, the private key of the owner will cryptographically secure its DID record.
Next, the user will get a public key corresponding to the key-pair generated in the DDO. Also, the DDO will have certain interacting services for the identity holder.
The user will get access to DID method specifications that will let him/her know just how they can register, update, revoke, or resolve their ID on the ledger.
Curious to learn about blockchain implementation and strategy for managing your blockchain projects? Enroll Now in Blockchain Technology – Implementation And Strategy Course!
Hyperledger Indy Use Cases
There are many possible Hyperledger Indy use cases for enterprises and individuals. Let’s see what they are –
-
Digital Documents
You can get any kind of document in digital formats, such as a birth certificate, passport, driver’s license, etc. The best part is that you can also have other important documentation on the network, specifically for enterprise blockchain use cases.
-
Password-less Authentication
Another one of the best Hyperledger Indy use cases is that it allows you to have a password-less authenticating process. In any sense, as passwords are far easier to crack, that’s why you can log in to a secure site with your fingerprint or any other form of biometric from your mobile.
-
End of Spam
With Hyperledger Indy use cases, you won’t get any more spam emails. Furthermore, you won’t have to verify your phone numbers every now and then either. With their super protective layers, no spam email can get through without your permission.
Want to know the basic and advanced concepts of Hyperledger development? Enroll Now: Hyperledger Fabric Development Course – Intermediate Level
-
Membership Management
This is more suited for enterprise companies as they can use Hyperledger Indy use cases to manage their decentralized membership model. Basically, the Indy agent will become your membership card, and you can use it anywhere that allows it.
-
Age Restrictions
Nowadays, the internet has become a place where everything is open to everyone. Sometimes, without restrictions, persons can misuse information. That’s why websites, devices, and services can work more efficiently with a proper age restriction.
For example, game developers can restrict minors from playing certain games or making certain in-game purchases.
-
Vulnerability Alert
With Hyperledger Indy use cases, developers can officially sign a software they develop before releasing it in the market. Thus, allowing a user to know whether the software is legit or not. Basically, with malicious copy software, hackers can get access to a user’s device.
But a user will get alerts right away if there is even some form of vulnerability in the software if they use Indy.
-
Employment Verification
While hiring a new employee, companies can easily do a background check with the help of a decentralized ID. So, if the employee claims to have previous experience or has proper certification, it will be associated with his/her ID.
Thus, the company can verify whether the credentials are true or not by requesting those documents only.
-
Provenance
Provenance is a major issue when it comes to businesses such as in supply chain or trading. According to the Hyperledger Indy tutorial, companies can easily get the provenance of a material. More so, even the consumers will get provenance of the products they are buying. It will offer a different level of trust among the manufacturer and the consumers.
-
Global Access
With help from this technology, you can move anywhere with one single ID. That means even if you go abroad, they can just use your ID to verify your credentials. So, instead of getting a new ID in another country or area, you can re-use your ID anywhere you are allowed to go.
Also, with DID, many people who don’t have access to identification will get their ID and enjoy the facilities that come with it.
-
Recovery of a Compromised Decentralized Identity
If somehow, you lose your identity, then you can recover it again. But you’ll need to have identity proof documents for requesting an identity provider. In reality, the identity provider will have every document on the ledger, and so you can match your credentials with it and get your ID again.
After that, identity-validators can validate your identity again with the help of biometric information. So, then you’ll get verified and will get access to your ID again.
Start learning Blockchain with World’s first Blockchain Career Paths with quality resources tailored by industry experts Now!
Conclusion
Hyperledger Indy is here to solve all our problems related to identities. There are so many people in the world that don’t even have identification. As a result, many can’t enjoy the facilities that come with it in a country. But with decentralized identities, it will be much easier to issue them an ID.
As you can see, Hyperledger Indy is full of features and is a well-structured platform. Thus, enterprises can easily integrate with the system and upgrade all their limited models to a much better ones.
If you are just a novice and want to understand different blockchain technology more thoroughly, we recommend starting with our free blockchain guide.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!