Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Blockchain
Hasib Anwar
- on October 02, 2019
Blockchain for Digital Identity: The Decentralized and Self-Sovereign Identity (SSI)
Identity is an essential factor in our lives. We live in a society where everything we do revolves around identity. And with easy access to it, our industrial aspects can truly shine. In reality, our identities are slowly leaving the paper-based old system and moving towards digital identity.
But, only making it digitized won’t solve the many issues that come along with it. Now that blockchain technology has been around for quite some time, it’s time we used the tech for digital identity as well.
To be frank, blockchain and digital identity are a really great pair. With new innovations coming in many fields, the identity sectors still lack digitization. And so, blockchain can surely help tackle all issues and gift us a decentralized identity solution.
So, I will talk about all of the extraordinary ways blockchain can be used for digital identity in this guide. So, let’s start!
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
Fundamentals of Identity
Identity surely is one of the basic rights of any human being. In reality, every human needs to have an identity in order to work in our social environment. Anyhow, the fundamental identity structure consists of –
- A first and last name.
- The birth date.
- Nationality.
There are also many other forms of identifiers such as passport numbers, driver’s licenses, social security numbers, etc. In reality, these forms tend to vary in countries.
Obviously, no one can state how much important identity is. More so, without any proper identification, you can’t really own property, use government services, vote, have a bank account, or even get yourself a job.
So, you’ll always need a way to have control over your identity or else it will be difficult even to prove who you say you are. Even though previously, the identity management sector used paper-based database systems, things have changed.
In reality, many countries are moving towards digital identity schemes that let us manage our identity easily. So, let’s see what digital identity is in the next section.
Want to understand the concept of decentralized identity? Enroll now in the Decentralized Identity Fundamentals Course!
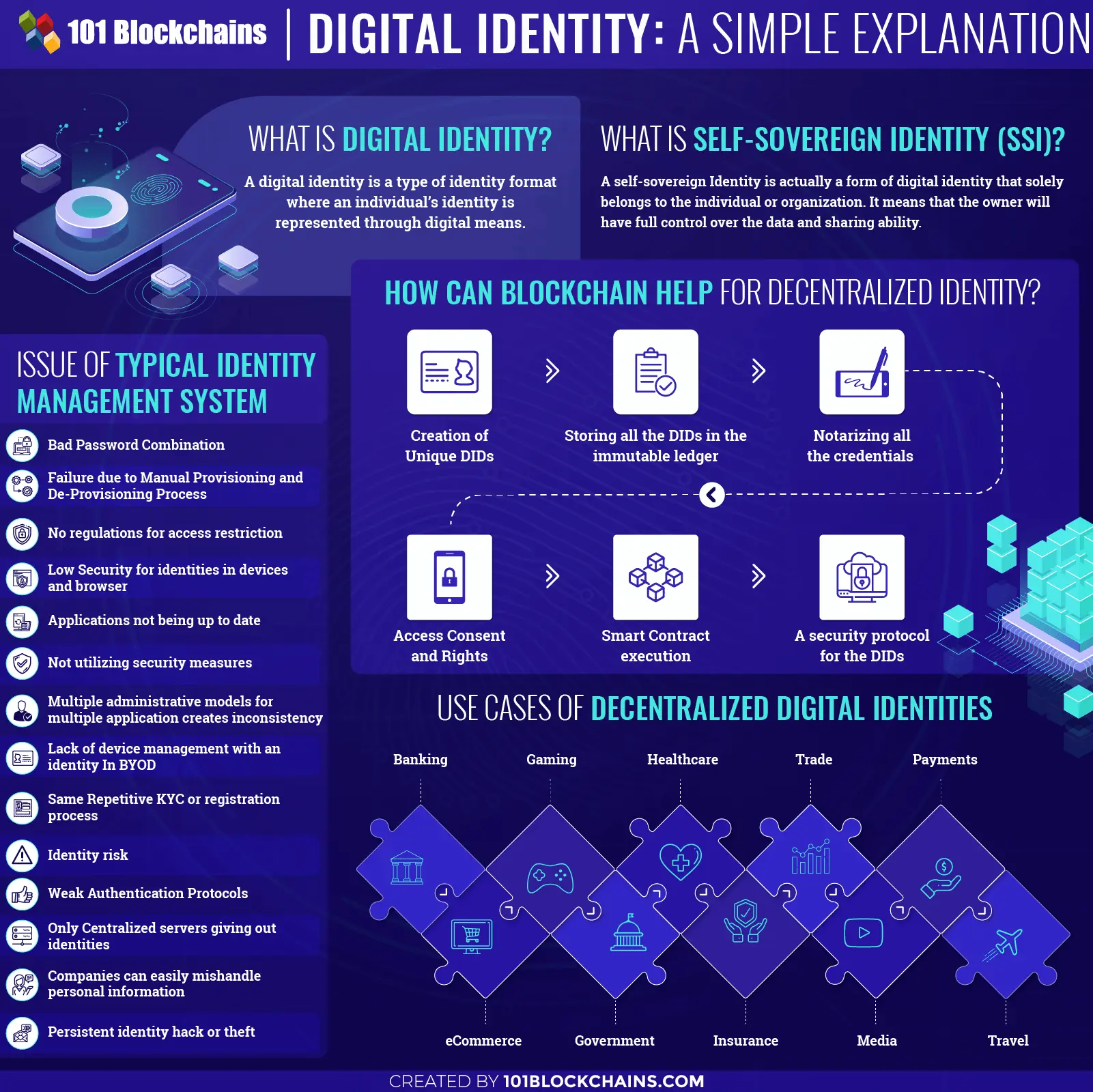
What is Digital Identity?
Even though the definition may seem a straightforward concept, still it’s not as easy as it looks. Let’s consider the fact that we all know who we are, but when it comes to others, they’ll need some form of a parameter to identify us. It could be our name or our face or any other type of information. In reality, this information is supplied to them by other sources.
So, when it comes to digital identity, any form of discrete information attached to you would be an “identity attribute.” Thus, you’ll see there are practically no bounds to how many attributes can define you.
For example, there are many biometric digital identity attributes such as what our face looks like, what our gender is, our fingerprints, voice patterns, etc. Other than these other digital identity attributes such as our names, birth date, marital status, or current address can also define us socially.
Other governmental attributes are obviously important, as well. So, in short, a digital identity is a type of identity format where an individual’s identity is represented through digital means. Furthermore, it can be atomic or can be cumulative as well. There are various levels of digital identity, and each one would give us a different perspective.
So, when you think about digital identity, it doesn’t only mean a single source of information but the combination of all the attributes. And that’s why it becomes challenging to handle. More so, the importance of digital identity is massive.
Digital Identity Management Systems at Present
Every kind of business depends on the evolving technologies that tend to take advantage of new opportunities. However, with every new tech comes a whole different set of challenges. In reality, the identity management system needs to have the speed to ensure every user gets their query solved in time.
More so, it also needs to have a higher security level. However, IT managers struggle hard to maintain both simultaneously. Moreover, attacks and faulty applications increase the difficulty of managing digital identity as well.
Thus, the importance of digital identity is more than ever. Anyhow, due to the lack of proper security issues, the scenario at present isn’t the best.
So, many users face identity issues that cause a massive problem in their social life as well. To ensure a proper management system, all the problems need to be solved fast.
Why Is Digital Identity Important?
The importance of digital identity is more prominent than ever for some major reasons. These are –
- Without a proper ID, getting access to education, banking, or health is difficult for people, and this includes refugees as well.
- Getting rid of a paper trail is more important as that system doesn’t offer people the best results due to the lack of speed and corruption.
- There’s no global cooperation with IDs, so, digital identity can enable that as it’s a digital-based identification.
As you can see, the importance of digital identity is absolutely massive.
Moreover, we use digital identity everywhere now. It not only makes our lives simpler, but it also increases efficiency. Moreover, in every app, device, or service, we have separate identification. And so, the importance of digital identity in those services is huge.
On the other hand, the importance of digital identity in the Enterprise sector is also prominent. In reality, enterprise companies need to have a full clarification of every single employee. It becomes a necessity to ensure efficiency in this sector, and thus, the use of digital identity technologies is increasing as well.
The Decentralized and Self-Sovereign Identity (SSI)
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2019/09/Digital-Identity-Blockchain.png' alt='Digital Identity Blockchain='0' /> </a>
Issue of Typical Identity Management System
-
Bad Password Combination
Let’s start with the most prominent issue of the identity management process. Most of the application offers a password-based login authentication system to enter it. However, the complexity of this process soon catches up.
In reality, all the applications have a certain expiration date for passwords. Moreover, even the requirements for new passwords keep changing over time. Thus, it becomes harder to keep track of new passwords and reset the old ones for the users.
As a result, the users go through “password fatigue” and use the same password for multiple applications. In many cases, they even repeat previously used ones, which increases the security risk for their identities.
Not to mention, using generic passwords also gives hackers a chance to steal their information without any issues.
Want to know more about the role of Blockchain in data protection? Enroll now in Blockchain and Data Privacy Masterclass
-
Failure Due To Manual Provisioning and De-Provisioning Process
When a new employee joins a company, the IT sector mainly gives that employee access to the core server, email accounts, file servers, and other internal networking systems. Basically, all the provisioning process is handled at the departmental level.
Thus, in many cases, the department administrator mainly grants access to the employee. However, as it’s a manual process, there are multiple human errors associated with it.
On the other hand, when the termination of an employee happens, there needs to be a restriction of access for that as well. But the de-provisioning process is also manual, and that’s why some employees may slip away with access to the central server.
In reality, this can be a major issue due to human-made errors. It would become an easy task to get into the server and steal valuable information without anyone even noticing.
-
No Regulations for Access Restriction
It’s absolutely necessary for the digital identity management system to know who has access to what type of data or applications. Moreover, they also need to determine which devices the user is using to access these data.
It’s more severe when it comes to cloud services. In reality, most digital identity management system doesn’t have proper regulations. Thus, many users can easily get access to information that they are not supposed to get.
Without proper control with regulations, it becomes very difficult to offer total security. Therefore, many users lose their valuable information and suffer greatly. You should have full access to your identity management system over other parties.
Moreover, this issue is more prevalent in centralized systems. And due to the lack of regulations, this sector is suffering greatly
-
Low Security for Identities in Devices and Browsers
We all use browsers and devices in every part of our life now. Basically, now that everything is on the internet, it’s absolutely normal to access your apps using mobile phones, PCs, or any other devices. However, the issue comes when you have too many access points to one app.
For example, you can log in to an app from the phone, tab, or PC. And most of the time, you can use a browser to do it. Therefore, you are setting up multiple risk points for your account.
In reality, hackers can easily hack into your browser or device to get control over the passwords and your personal information.
Thus, it becomes absolutely necessary to have a good security system for all the devices you use. So, without a proper identity management system none of your IDs are absolutely secured.
Want to learn about security in blockchains? Enroll Now in Certified Blockchain Security Expert (CBSE) Course
-
Applications Not Being Up To Date
You may think what updating applications have to do with identifying risks? Well, in almost all the applications, the developers initially setups a security measure to protect information.
However, no application is perfect, so bugs or loopholes are evident when multiple users start using it. So, when a user detects a bug and reports it, the developers roll out a security patch for it. However, in many cases, the developers don’t update the application soon enough.
Moreover, users also don’t update their applications to the latest version as soon as it’s available. Thus, hackers get a chance to use the bugs or loopholes to get into the system and steal identity information.
In reality, the same goes for enterprises as well. An enterprise company needs to keep all of its applications up to date with proper security patches. Or else it might be late.
-
Multiple Administrative Models for Multiple Application Creates Inconsistency
In reality, cloud applications are becoming cheap, and more enterprises are using them. Thus, they take in many SaaS applications under their wings. However, even though there are multiple operational groups maintaining them, there’s no single point of reporting for every kind of application.
What I mean by it is that an enterprise company can have multiple applications. However, if all the applications run on different administrative models, it becomes harder to keep track of the users. More so, getting the right reporting for all of these in a different context is harder to manage.
Thus, having all the applications run under the same administrative model can solve the issue. But due to the lack of an identity management system, employees can exploit the situation.
And so, switching to distribution channels can really solve the issue here.
-
Not Utilizing Security Measures Properly
Without the use of proper security channels, it would be hard to keep track of all the users. In any issue, there needs to be an instant alert system. However, today’s digital identity management system seems to lack that.
On the other hand, their system also doesn’t offer any proper reporting measures or preventive measures. Moreover, the storage system isn’t immutable. If anyone gets access to that, he/she can easily abuse other people’s identities.
And this is how identity thefts happen. More so, the increased level of cyber threats tends to happen for this reason as well. In most cases, the platforms are so easy to manipulate, that no user is ever safe from the cybercriminals. Thus, the identity management system needs proper security measures.
-
Lack of Device Management with an Identity in BYOD
Another grave issue of the identity management system is the lack of device management in certain BYOD. In reality, BYOD means Bring Your Own Device. Many enterprises now let their employees bring their own device into the workplace and use it.
However, they tend to forget about the threat that also comes with it. Usually, the enterprise has firewalls or other security services in every device they provide the employees. But when it comes personal devices, it obviously doesn’t have the security measures as it needs.
And so, when an employee connects to the company’s network, he/she is risking exposing their identity for hackers.
Thus, if an only single device is hacked, then the whole network is compromised as well. In reality, enterprises need a system that would only allow registered personal devices to connect to the server.
Aspiring to make a lucrative career as a blockchain expert but not sure how? Check the detailed guide Now on How To Become A Blockchain Expert
-
Same Repetitive KYC or Registration Process
Repetitive KYC processes are also another major issue for the identity management system. Due to the multiple platforms being separated from one another, we have to register several times for every service we take.
For example, when we open a bank account, we have to register. On the other hand, we do the same thing for insurances, going abroad, taking loans, etc. These repetitions of the same KYC protocols open up multiple access points to our information.
And thus, digital identities are vulnerable with increased privacy breaches. On the other hand, it’s more problematic for the users as well. They have to go through the same registration process over and over, which wastes time.
-
Identity Risk from Online Platforms
Many of us tend to share information about us online on various platforms such as when we shop online or register for a service. Obviously, without registering, we can’t possibly get access to these platforms.
But the problem increases when these platforms don’t have the proper management tools to handle our information.
Moreover, many of us don’t understand that puts our identity at risk along with data breaches. Furthermore, many social platforms or e-commerce tend to have more control over our information. Most of these platforms are centralized, and the security isn’t up to the mark.
Moreover, without proper management, it’s evident that someone would eventually abuse our information.
-
Weak Authentication Protocols
The authentication process is the major concern for digital identity management system nowadays. But with only a single factor authentication process, no one can fully have total security for their identity.
In reality, only offering passwords isn’t enough anymore because it doesn’t have enough layers to stop hackers. That’s why many companies now use two-factor authentication processes. In reality, these mainly offer email or SMS pin numbers or even biometrics.
However, the hackers are innovating as well, and many of the two-factor authentications isn’t stopping them anymore. They can now breach through the two-factor authentication process as well.
So, to make sure that hackers can’t get into the system, the enterprise needs to use a strong multifactor authentication process. Other than this, there is evidently no way to stop cybercriminals from exploiting our information.
Start your blockchain journey Now with the Enterprise Blockchains Fundamentals
-
Only Centralized Servers Giving Out Identities
Following the traditional method, only centralized servers can issue identities. These identities are basically country-specific. However, as these centralized servers have total control of who they are issuing the identity, many citizens are left without an identity.
Well, according to a report, more than 1.1 Billion people in the world don’t have any identification attribute. So, without any valid ID, they can’t even have a bank account. In the long run, the number of these people will keep increasing if we don’t leave the traditional path.
Moreover, these centralized institutes don’t even make an effort to give proper citizen rights to all these people as well.
-
Companies Can Easily Mishandle Personal Information
Just take a look around yourself. We live in a digital world where every company would exploit your information for their selfish reasons. More so, now every company needs registration for you to give access.
But what they don’t tell you is how they misuse your data and manipulate you in everyday life.
For example, let’s take the Facebook case. The app “This Is Your Digital Life,” surveyed multiple people and scammed them, saying it was purely academic. More than 300,000 users downloaded the app and used it.
However, what they didn’t know that the app would also collect information from other people in their contacts as well. Even though the app sited this in terms of services, still who really bothers to read them, right?
Anyhow, more than 87 million people lost their personal information to the app.
Thus, there need to be strict protocols and security measures to limit other companies from exploiting identity information.
-
Persistent Identity Hack or Theft
Last but not least, the persistent identity hack issues is haunting the digital identity space for a long time. In reality, there are multiple reasons for it to happen. In 1997, a woman named Bari Nessel would con people saying she is hiring them for a job.
She would collect their personal information along with their bank account info as well. By doing so, she could misuse many people’s credit cards.
But almost recently in 2017 a credit reporting company was hacked and stole user’s credit card information, social security numbers and many more.
So, how do you these attacks happened? Well, most people trust many third parties to handle their information, and this gives rise to data hacks even more.
Blockchain and Decentralized Identity
What Is Decentralized Identity?
Well, the short answer to this question would be that, there would be no centralized institute issuing or having claim over any kind of identity. Your identity would be solely yours to claim. Moreover, the added level of security that comes with decentralized ones would truly amaze you.
Anyhow, no third party or any other institute can misuse your digital identity anymore. So, you would need to maintain it.
Digital Identity Blockchain: How Can Blockchain Help?
Blockchain technology can be a great solution for decentralized identity. In reality, blockchain for enterprise can easily power the framework of the decentralized identity. Not only does it offer a readymade infrastructure, but it also offers security for it.
So, if the enterprise starts to use it, it will definitely solve the issue that comes with third party companies misusing information.
So, let’s see how blockchain can really help in this sector?
Start learning Blockchain with World’s first Blockchain Career Paths with quality resources tailored by industry experts Now!
-
Creating DIDs
I think you already know that blockchain addresses are extremely unique. And you can use these addresses for making DIDs. Moreover, these are all cryptographically secured, and the owner generates it themselves.
-
Registry for All DIDs
Another great digital identity blockchain platform usefulness would be using it as a DID registry. Basically, you can store all the information of the IDs to the immutable ledger storage. This way, no one can access your ID anytime and even steal the information.
-
Credential Notarization
It’s similar to putting seals on your ID. Here, the platform can offer to put a hash address to that information on the digital identity blockchain platform. However, it doesn’t mean it will only store the credentials on the ledger.
It would mean that it would act as a timestamp and moreover, offer an electronic seal. For example, let’s say a university would provide the hash for a diploma on the platform after the student graduates. It will help the student to know when the diploma was issued along with proof of his certificates.
Thus, when he uses the certificate for a job or other purpose, he can show that this is the certificate that had the hash function from the university.
In reality, it can be a great way to change how people handle the certification from any respected university. Moreover, it gets rid of the falsifying certificate issues that many companies face while hiring a new employee.
-
Consent and Access Rights
You can also use the digital identity blockchain platform to control who can access your credentials and who can’t. For example, you might want to share some of your information on various platforms but maybe for a certain amount of time.
You could also give access to companies that you want to work with to check if you have the notarized credentials or not. Anyhow, you can do that in the form of transaction with an expiration date. So, when it expires, it would be back to the way it was.
On the other hand, the company that you grant access would then have to delete the information and prove it on the platform that they did so.
-
Using Smart Contract Features
There’s plenty of use of smart contracts. Moreover, you’ll need your identity every time for official contracts of any sorts. For example, in insurance, healthcare, or any form of services. So, you can use your identity as a proof in smart contracts triggering a payment system along the way.
If you are new to smart contracts, you might not be sure of its capability. Check the detailed guide Now on Smart Contract Use Cases
How Does Decentralized Identity Work?
Well, you know how you can use decentralized identity using blockchain, but how does the system really work? In reality, there’s a lot of promises to deliver and make sure a user gets what is advertised.
But can the platform really do that? Usually, the system would have several layers where each will play its role in maintaining the DID. Let’s see what these are.
-
W3C Decentralized Identifiers
Using this, the users can create their very own decentralized identities and control them without any central or third party restrictions. Here, these DIDs would be linked to their Decentralized Public Key Infrastructure metadata.
Usually, JSON documents with authentication information, public key materials, and service endpoints make up the metadata.
-
Decentralized Systems
In reality, every single decentralized identity would be rooted in the digital identity blockchain platform. Moreover, the platform would offer the mechanism and features needed for DPKI. In many cases, a particular DID could support multiple types of platforms.
It will give the users a bit more flexibility if they want to switch to another form of ledger system.
-
User-Agents
Mainly these are applications that would help you to use the identity. User agents would make sure you can create, manage the control in a user-friendly way. Moreover, it would also help you to validate or sign any DID connected claims.
In reality, this app can also offer a wallet feature that would help you to pay on the digital identity blockchain platforms.
-
Universal Resolver
It’s mainly a server that would use a set of DID drivers to offer a resolution and lookup feature on the digital identity blockchain systems. Furthermore, it would return the DID Document Object that is directly connected to the DPKI.
-
Identity Hubs
This is just a speculation, but it should also offer identity hubs made of edge instances and cloud storage. Basically, these would act as storage for smart devices such as PCs, mobile phones, and smart speakers.
A Sample Scenario
Let’s look at a sample example that would help you see how this new form of identity can work in real life. Imagine you recently graduated from any college. With the help of decentralized identity, you can ask for a digital copy of your certificate from the university.
In reality, the university would issue this digital copy against your DID. Now, using that you can present it to anyone, for example, to an employer. The employer can then verify whether the digital copy is real or not using the time of the issuance and the status of it.
So, basically, there are a few steps to make it work.
Step-1: The University signs the digital copy of the certificate and uses the User-Agent to connect it to the student’s respective identity.
Step-2: The User-Agent will then store the data to the student’s personal data vault. Moreover, the student can access the information, identity hubs, and Universal resolver using the Agent as well.
Step-3: In a case where the student would need to present the certificate, he/she can present it to other parties through the Agent.
Step-4: Other parties can verify the creditability of the certificate from the platform itself.
Want to understand blockchain terminologies? Check Now Blockchain Glossary For Beginners: A-Z Blockchain Terms!
What Is Self-Sovereign Identity (SSI)?
Well, explaining it is a bit tricky. In reality, it would mean that an individual would have the sole ownership of their digital and analog version of identities. On the other hand, organizations can also have this much privilege as well.
So, if a user has Self-Sovereign Identity, he/she can control who can access their information, maintain their identities themselves, use it for verifying their identity online, and many more.
Because of the nature of this identity, the best technology for it would be blockchain. In reality, blockchain is decentralized, and that indicates that there’s no third party in the mix.
However, for this system to be fully functional and successful, it needs to have some principles. Thus, using the principles of blockchain-powered Self-Sovereign Identity platforms can work side by side GDPR law.
What Are the Guiding Principles of Self-Sovereign Identity?
There are some unique guiding principles when it comes to Self-Sovereign Identity. Basically, there are ten principles of SSI that every platform needs to offer no matter what. Let’s see what they are –
-
Existence
All the users need to have an independent existence in the platform. Basically, this came from the concept of “I.” Here, it implies that all the users on the platform have to have independent existence even in digital form as well.
-
Control
Here, the users would need full control of their identities. However, there’s a different meaning to it as well. In reality, there are many scenarios where complete ownership of the Self-Sovereign Identity isn’t possible at all. But in those cases, the user can limit how the other parties would handle their identity.
-
Access
A Self-Sovereign Identity needs to offer full access to its user. So, any user should access their data and any kind of other claims without relying on any intermediaries. But, in no way, they can modify all the data, as the data would already have signed verification that can’t be altered.
-
Transparency
All the systems or algorithms handling the identities need to be transparent. Without an open system, the user can’t monitor if the Self-Sovereign Identity platform is managing their identities correctly.
-
Persistence
For a Self-Sovereign Identity platform, all the identities have to be long-lasting. It means even if the system went through a system upgrade, the user could keep all of his/her previous data as the way they were.
-
Portability
All the user can transport the identity when they need it. In reality, this feature would ensure that they can export their identities and use them when in certain scenarios.
-
Interoperability
In reality, the Self-Sovereign Identity would need to be acceptable anywhere around the world. Thus, without proper interoperability, the identities would lose flexibility.
Excited to learn more about interoperability and portability read here A Guide to Cloud Interoperability and Portability
-
Consent
If for any reason, a third party needs to access the identity, then the user would have to have full consent. Without permission, no party can access their identities in any matter.
-
Minimization
There’s no need to overexpose anyone’s identity. Maybe someone wanted to know about the age of a user. So, in that case, the system should only disclose the age and not the exact birth date.
-
Protection
No matter what happens, every user needs to have full rights on their Self-Sovereign Identity. So, the platform needs to maintain it no matter what.
Start learning Blockchain with World’s first Blockchain Skill Paths with quality resources tailored by industry experts Now!
Use Cases of Decentralized Digital Identities
-
Banking
Well, banking is the first decentralized digital identity use cases you can find. In reality, the banking sector deals with a lot of identity-based issues such as false identifications, identity thefts, repetitive KYC protocols, and many more.
On the other hand, if they start to use decentralized digital identity, then almost all of their problems get an easy solution. Thus, when you want to open an account, you won’t have to deal with a lot of issues. Instead, you can just grant the bank access to your identity, and they can verify all your credentials from that.
-
E-commerce
In e-commerce, you’d need to have a proper identification to prevent frauds. In reality, the e-commerce section deals with a lot of fraud product selling issues. Many users pay money to buy authentic products. But instead, they get fake one or completely different ones from what was advertised.
This happens due to the lack of proper protocols when signing up in that e-commerce. Thus, decentralized identify foundation can ensure the proper verification needed for safeguarding this sector.
-
Gaming
The gaming industry is huge. But I think you might know it by now. Anyhow, this industry deals with a lot of identities of the gamers. However, in many cases, the industry fails to offer security to the gamers.
Moreover, many apps have in-app purchasing features, which needs security because it asks for credit card numbers. Thus, decentralized digital identity can shape it using regulations from decentralized identity foundation.
-
Government
Government is a huge sector for decentralized identity foundation companies. In reality, the government issues a lot of official identification documents for the citizens. However, the process of handling it needs a lot of catching up to do.
The process of issuing is slow and full of errors. Moreover, citizens have very little ownership access to their very own identity. Thus, government services can highly benefit from decentralized digital identity to reduce paperwork, corruption, and offer security.
-
Healthcare
The healthcare industry will highly benefit from decentralized digital identity. In reality, almost all of the healthcare institutions have no security for patient’s information. As a result, many use them for their private research or get access to sensitive information without consent.
On the other hand, decentralized identity foundation can help healthcare to safeguard all the health-related data. Moreover, patients would get full control and privacy they deserve, as well.
-
Insurance
Too much paperwork and the false insurance claim is what insurance company’s need to battle with. In reality, the process of filing an insurance policy is a lot of work for both the insurer and the insured client.
Moreover, in many cases, people try to be fraudulent for insurance claims. Also, the process of verifying all the credentials are time-consuming as well. But with the help of decentralized identity foundation, every single problem would be solved.
-
Loan
You need to have the proper identification along with having the proper credentials to get a loan from any company. If you don’t meet up with the requirements, you’ll simply won’t get the loan. However, to get a loan, many people to show false credentials. And due to that, the company loses the money as it can’t get the user to pay the debt.
However, with the help of decentralized identity foundation, they can prevent it and even offer instant loans to the right candidate.
-
Media
The media reeks of bogus contents nowadays. In many cases, you see a lot of fraudulent accounts clouding the media space. However, with decentralized digital identity, the rightful artists will get the payment they deserve.
On the other hand, any kind of bogus content or fraudulent accounts can never cloud the media industry ever again. Moreover, no one can make money with copied contents from other artists as well. Thus, the system would be fairer.
-
Payments
Dealing with money always comes with a risk of the unknown. In the case of enterprises, they need to check whether the other party is who they say they are. However, the typical verification process is not helpful at all.
Thus, these enterprises can get help from the decentralized identity foundation. With the use of proper identification and verification process, it’s quite simple to work with the right client. Also, sending payments to the right people would be much easier as well.
-
Travel
The new identity model can help out the travel industries as well. Basically, this would deal with stolen reward points issue along with fraudulent reservations. If the travel industry starts to use this new form of identification, it can also simplify the passenger processing system as well.
You can carry your identity, and they can just match it right on the spot. It would reduce the processing time and increase efficiency.
Want to become a Blockchain Engineer? Start learning Blockchain with World’s first Blockchain Engineer Career Paths with quality resources tailored by industry experts Now!
Suitable Enterprise Platforms for Decentralized Identity
There are some enterprise blockchain platforms on the market that are suitable for the decentralized identity management platform. In reality, these enterprise platforms offer the best of the best services for any identity issues. So, let’s see what they are –
-
Corda R3
R3 comes with two versions of Corda – one’s for enterprises and another a regular version. Basically, the Corda enterprise would be more suited for your decentralized identity management system. Even though Corda enterprise is a commercial version, but it’s still fully compatible with Corda.
In reality, Corda offers a higher level of quality and robust infrastructure for any kind of platform. As it’s also a permissioned platform, it would be a perfect choice for your decentralized identity management system.
Even though many of you may think that Corda is just suited for the financial sector, it can offer a very different blockchain model for other sectors as well.
Let’s see what the Corda platform has in store for you –
- Corda’s application blockchain firewall will protect all your sensitive information from any outside influences.
- It also comes with high-availability and governance features to help you out.
- If any disaster happens, you’ll get real-time reports and have options to fix them as well quickly.
Want to understand the basics of Corda Development? Check out this ultimate Beginner’s Guide to Corda Development
-
Hyperledger
Hyperledger is an enterprise blockchain project that has multiple projects under its wings. It started the journey back in 2016 and now is one of the popular names in the blockchain niche. In reality, Hyperledger offers some projects that are more suited for decentralized identity management.
For example, their Hyperledger Indy is a distributed ledger that solely works with digital identity. Moreover, with this one, you’ll get components, libraries, and tools to develop your decentralized identity management system.
Other than this, you can also use your identity on other platforms as well.
Just recently Hyperledger also uncovered another project called Aries. Although it’s in the incubation phase, still it would act as a toolkit. This is similar to developing your own platform with a set of features on the module.
Basically, they offer –
- Permissioned blockchain platforms and open-source toolkits.
- High level of performance with added scalability.
- Only need-to-know basis data availability.
- Query languages for searching the ledger.
- Plug and play modular structure.
- Higher safety measurements for sensitive information.
Want to learn the basic and advanced concepts of Blockchain and Hyperledger Fabric? Enroll Now: Getting Started with Hyperledger Fabric Course
-
Ethereum
Ethereum has been around for quite a lot of time. Vitalik Buterin founded the platform for enterprise-grade usage. However, enterprise blockchain is permissionless. And that could be an issue for the decentralized identity management system because every single user needs to have privacy.
On the other hand, to offer privacy for enterprise companies, Ethereum does offer a private version of its platform through Enterprise Ethereum Alliance. So, using that version, you can definitely develop a full proof decentralized identity management system.
Now let’s see what features you will get from this platform –
- They offer an open-sourced platform.
- You will get authoritative support from the EEA for any kind of Ethereum based project. It will help in finalizing the guidelines and standards.
- EEA provides governmental support for projects under them. So, if another organization developed the features you need, then EEA will support you to get that as well.
- It also comes with constant updates from the public version.
- They also offer an array of standards to make it easy for you to develop any kind of platform.
Excited to learn the Ethereum Development Fundamentals? Enroll Now: Ethereum Development Fundamentals
Popular Projects working on Digital Identity
There are multiple real-life digital identity solutions at work now. Now, you’ll see which digital identity companies are working on this new identity model scheme.
Sovrin
Sovrin is one of the popular projects offering a self-sovereign identity for the users. In reality, it’s a non-profit organization that solely works with decentralized digital identity solutions. With this, you can get finally get personal control, trust, and easy to use digital identities.
According to them, they offer a new standard for digital identities. In reality, you can even get a digital copy of your driver’s licenses or personal IDs.
Basically, it’s a metasystem that allows organizations, people the freedom to use any application without worrying about their identities. Moreover, Sovrin also happens to have verifiable credentials options.
Civic
In reality, Civic is a personal identity verification process that uses blockchain technology to offer digital identities. Anyhow, if you use the platform, you can create your very own virtual identity along with storing additional information as well.
However, you’ll have to verify all your credentials before you can store in on the digital identity solutions. At present, you’ll get four kinds of solution for growing your business on these digital identity companies.
- Secure ID Platform would let your users access your website through a secured identity.
- Reusable KYC provides satisfaction in any kind of KYC requirements.
- Automated Retail can give you access to smart vending machines.
- All kinds of investment, advisory, and business relationships would get individual ID Codes.
- It also offers Passwordless Login
uPort
With uPort, you can experience the full freedom of control over your identity. It’s built on Ethereum, and all the users can create their very own digital identity solutions on it. Moreover, they can also request and send credentials, manage their own data and keys, sign transactions, and many more.
What you’ll get –
- Credentials: Basically, it’s building an ecosystem of identity credentials. With your app, you may request for credentials of other users, but it’s up to them whether they’ll share it or not.
- Protocols: With this type of digital identity companies, you’ll get access to a lot of protocols and messaging options form the app.
- Tools: They have a modular structure with the developer’s tool, so it’s very simple to use.
Bloom
Bloom offers a different approach to digital identity solutions. In reality, BloomID is the secure identity you need to work in your business. In reality, you’ll get a lot of features that come with BloomID. These are –
- You can safeguard your personal information with blockchain and prove their creditability without overexposing any of your information.
- Additionally, you can choose what to include in your identity and how you will use it.
- While building up your decentralized identity using these digital identity companies, you can earn stars that would increase your reputation.
- With their help, you can verify your identity anywhere around the world.
Other Projects to Check Out
KYC Chain
KYC Chain is one of the digital identity companies that use blockchain to power their platform. Mainly their goal is to offer verifiable documents, data, or identity claims that are needed for any KYC processing.
On the other hand, for data privacy, they offer users the sole ownership of their private keys. So, you can decide who can see your data and who can’t.
SelfKey
SelfKey offers self-sovereign digital identity solutions, which would allow you to create, own, and control access to your identity. Furthermore, the platform would need a KEY to function. It’s a utility token that you’ll need to get access to the system.
The best part about this platform is that it can help you verify your identity and notarize any ID documents online. Moreover, you can also get citizenship based on your investment and other factors.
Nuggets
Nuggets is one of the digital identity companies that offer biometric identities along with payments. When you start using their app, you can access identity verifications, payments, and logins using a single biometric source.
According to them, they don’t even have any access to your personal data. So, you can choose to share it with any respected user if you want. You could think this platform as digital identity solutions that are for payments mainly.
Jolocom
Jolocom is another digital identity company that offers self-sovereign identities to individuals and organizations. Apparently, their IDs are interoperable, meaning you can use your identity on any other platform as well.
Anyhow, you have the sole control of your encrypted personal data and how you’ll use it. So, there’s no option for any third-party intervention.
Concluding Thoughts: A Glimpse of the Future
You might already experience it every single day that the world is going through a massive digital transformation. And now, the physical and digital world is merging into one single reality. Thus, it’s evident that the world needs a new way to maintain all the digital identities.
Specifically, the model should have security and privacy in every aspect. That’s why decentralized digital identity is the perfect solution for this. In reality, it not only offers full control of your individual identity rights, but it also makes managing it easier.




1 Comment
Didn’t know blockchain could make digital identity so simple. The content was really helpful and insightful.