Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Guides
Diego Geroni
- on May 05, 2021
An Introduction to Public Key Cryptography
Any individual in the domain of software development or a tech enthusiast must have heard about the applications of cryptography. For software developers, cryptography is an integral aspect of signing messages, signature verification, use of certificates, and encryption of payloads.
As a matter of fact, cryptography is an essential requirement for modern applications and enterprise solutions. With the large volumes of sensitive customer data and confidential business information being exposed to various vulnerabilities, it is important to reflect on different cryptography techniques.
Public key cryptography or asymmetric cryptography is undoubtedly one of the prominent cryptographic techniques used in present times. So, what is public-key or asymmetric cryptography? The following discussion provides a detailed account of public key cryptography explained with examples, characteristics of the algorithm, and prominent advantages.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
What is Public Key Cryptography?
The first point of discussion in any introduction to public key cryptography refers to its definition. As the name implies, the type of encryption involving public key is known as public key or asymmetric cryptography. So, why is asymmetry included in the definition? Asymmetric cryptography involves the creation of a public key and a private key.
The public key is utilized for encrypting the message of the sender, while the private key helps the receiver in decrypting the message. There are no profound historical accounts of the implementation of public-key cryptography as it is a comparatively new concept. Symmetric cryptography has been widely accepted for use in large financial enterprises, military, and government agencies for classified communication purposes.
However, the gradual growth in the number of unsecured computer networks in recent times presented the need for implementing cryptography on a broader scale. Symmetric cryptography turned out unsuitable for large-scale implementation due to challenges in key management. As a result, the public key cryptography example served as the most prolific solution for the setbacks in symmetric cryptography.
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src=src="https://101blockchains.com/wp-content/uploads/2021/04/introduction-to-public-key-cryptography.png" alt="introduction to public key cryptography" border='0' /> </a>
Symmetric Vs Asymmetric Cryptography
Before diving further into the details of public key encryption, it is important to take note of the difference between symmetric and asymmetric or public key encryption. The differences can help you understand the distinct advantages of public key in blockchain over symmetric encryption. In the case of symmetric cryptography, one key is used for encryption as well as decryption.
The key serves as the shared secret for multiple participants involved in a transaction. Furthermore, the risks of leaking the secret key also increase profoundly with the rise in the number of participants in the transaction. For example, if any participant’s system is compromised, any individual with the secret key can decrypt all the messages to other network participants.
Therefore, compromises in shared secrets in any particular location jeopardize the security of the whole system. So, the need to use a single shared key and implement secure approaches for transferring it serve as a prominent setback with symmetric cryptography. As a result, the asymmetric encryption method started to find its roots in the mid-70s as researchers working on finding different approaches for creating and securely moving keys.
In the case of public key cryptography, every party in the transaction has a pair of keys, including a public key and a private key. The most prominent improvement with public key encryption is the fact that the public key does not serve as a shared secret. Participants in a network or transaction don’t have to keep the public key hidden by multiple parties. As a matter of fact, participants have the privilege of sharing their public keys with others.
Want to learn about the differences between Public and Private Keys? Checkout Public vs. Private Keys deatiled presentation now!
Issues Addressed by Public Key Encryption
Public key cryptography notes also focus on the issues that it resolves. It is important to observe the reasons for employing public key encryption. Internet traffic moves information through various intermediate computers in a network. Therefore, third-party agents could intercept the continuously flowing internet traffic to obtain sensitive information through malicious ways. The issues addressed by public key encryption provide a formidable impression regarding its benefits.
Here is an outline of some of the common threats that you resolve with public key encryption.
- Tampering
Tampering is one of the formidable concerns for information security in modern times. It involves changing or replacing the information in transit before it goes to the recipient. For example, malicious agents could change a person’s details in their resume or modify an order for products.
- Eavesdropping
Public key cryptography can also help in resolving the issues of eavesdropping in information security. Although the information remains intact in eavesdropping, the privacy of the information is compromised. The examples of eavesdropping are evident in incidents of intercepting classified information or collecting credit card numbers.
- Identity Theft
Identity theft is a critical issue in the modern information security landscape. With malicious agents impersonating other individuals, identity theft poses serious consequences for digital security. The first type of identity theft includes spoofing, according to which a person could pretend that they are someone else.
For example, an individual could pretend that they have an email address. Another type of identity theft is clearly evident in the incidents of misrepresentation, which involve a person or organization posing as something they are not. For example, an organization that receives orders but never delivers any products could showcase its identity as an online furniture store.
Public key in blockchain helps in providing the desired protection against such types of attacks by leveraging four important factors. The factors include,
1. Encryption and Decryption
Encryption and decryption are probably the most common terms you would come across in a public key cryptography example. Both of them help two parties to cover up the information transferred between them. The sender scrambles the information (encryption) before sending, and the receiver unscrambles the information (decryption) after receiving the message. During the process of moving from the sender to the receiver, the information is not readable by any unauthorized party.
2. Authentication
Public key cryptographic technologies also emphasize the value of authentication. Authentication is essential to enable the recipient of a message to find out the origin of the message through the confirmation of sender’s identity.
3. Tamper Detection
The next significant feature outlined in public key cryptography notes emphasizes tamper detection. Public key encryption ensures that the recipient of a message can verify that it has not been through any modifications. Public key encryption enables easier detection of any attempts for modification or substituting information during transit.
4. Non-Repudiation
Non-repudiation with public key encryption ensures that the sender could not claim that the message was never sent in the first place at some time in the future.
Working of Public Key Encryption
So, what does public key encryption look like actually in the real world? The following public key cryptography example can help you find out how it works.
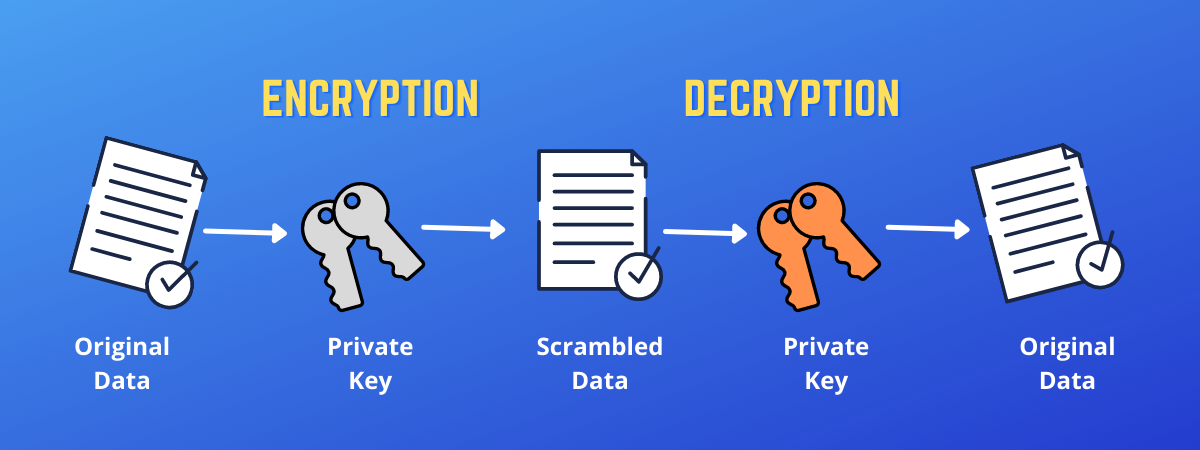
- The sender John wants to send an important business document to Mary, his colleague in the same company. The business document is highly confidential and should be seen by Mary only.
- So, John uses his public key for encrypting the business document before sending it to Mary.
- Now, the business document has turned into scrambled data and is completely unreadable for any other employee in the company.
- Mary could receive the message and use her private key for decrypting the message sent by John,
- Mary could retrieve the original data sent by John with the help of her private key.
See how simple it is to implement public key cryptography!
Now, it is important to find out what are the important components that define the working of public key encryption. The significant components in public key or asymmetric cryptography include plain text, ciphertext, encryption algorithm, decryption algorithm, and most important of all, the public key and private key. Each component has a unique function in the overall public key encryption infrastructure.
- Plain text, as the name implies, refers to the message that is interpretable or readable for any individual. The plain text serves as the input for the encryption algorithm.
- The ciphertext is the output generated from the encryption algorithm. The scrambled message is completely illegible for anyone.
- The encryption algorithm and the decryption algorithm play the most critical role in public key cryptography. An encryption algorithm helps in converting plain text to ciphertext. On the other hand, the decryption algorithm takes in the ciphertext as input alongside the matching key pair for producing the original plain text.
- The public and private keys are important in the public key ecosystem. It is possible to use any of the keys for encryption when you can use the other for decryption.
Important Traits of Public Key Encryption
The content of public key cryptography notes is incomplete without reflecting on the important characteristics that are unique for public key encryption. Here are some of the notable features that you can find solely with a public key or asymmetric cryptography.
- Public key encryption involves the use of distinct keys for encryption and decryption. The use of different keys for encryption and decryption helps in differentiating public key encryption from symmetric cryptography.
- Every recipient has their own personalized decryption key, known as the private key.
- Recipient must also showcase an encryption key, known as their public key.
- Public key cryptography also relies on proving the authenticity of public key to avoid concerns of spoofing by malicious agents. The public key encryption system leverages the services of trusted third-party providers for verification of ownership of public key.
- The next important characteristic of public key encryption relates directly to the algorithm. The public key cryptography algorithm for encryption must have ideally complex traits for preventing attackers from deriving the plaintext or unscrambled message with the help of ciphertext or scrambled message and the encryption public key.
Another striking highlight that showcases the value advantages of public key cryptography refers to the relationship between public and private keys. Both of them are mathematically related to each other. However, it is not possible to derive the private key from the public key. As a matter of fact, the most crucial component in the public-key ecosystem deals with the design of the relationship between public and private keys.
Start your blockchain journey Now with the Enterprise Blockchains Fundamentals
Public Key Cryptography Algorithms
As you must have understood by now, public key encryption depends profoundly on algorithms for encryption and decryption processes. Presently, there are around three different types of public key cryptography algorithm. However, the most notable mention among all the algorithms used for public key encryption refers prominently to the RSA algorithm.
Developed by Ron Rivest, Adi Shamir, and Len Adleman, the RSA algorithm offers a wide collection of cryptographic algorithms. It has a reputation as a reliable tool for supporting public key encryption. As a matter of fact, various protocols such as SSL/TLS, OpenPGP, secure shell, and S/MIME utilize RSA for cryptography.
RSA has found widespread application as a public key cryptography algorithm with browsers that have to establish secure connections over the internet. In addition, the most common tasks performed in systems connected to the network involve RSA digital signature verification. It can offer profoundly reliable levels of security. RSA algorithm presents difficulty in factoring large integers derived as products of two large prime numbers.
Even though the multiplication of the two numbers is easy, it is not an easy task to find out the original prime numbers. The applications of RSA in public key cryptography explained properly would show that generating the algorithms for the public and private keys is the most complicated task of using RSA for cryptography. The security with the RSA algorithm depends on the difficulty in factoring large integers.
Final Words
On a concluding note, it is quite clear that public key cryptography is an essentially flexible and prolific tool for information security. The advantages of public key encryption are clearly evident in the opportunities for dealing with prominent internet-based attacks. In addition, public key encryption also brings the assurance of complete control over the security of your own data.
It reduces the need for managing multiple keys, like in the case of symmetric cryptography. Public key encryption enables recipients to prove their ownership of the private key without revealing their details. Furthermore, the substantial breakthroughs in the world of computing have established the foundation for the arrival of new algorithms.
If you’re aspiring to build a career in blockchain security, we recommend you to enroll in the Certified Blockchain Security Expert certification program. It will help you learn more about public key cryptography and become a blockchain security expert!
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!