Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Blockchain
Gwyneth Iredale
- on April 23, 2021
Blockchain Cryptography: Everything You Need to Know
Blockchain has emerged as one of the most innovative application models with capabilities for integrating consensus mechanisms, distributed data storage, digital encryption technology, peer-to-peer transmission, and other computing technologies. It has provided an effective platform for secure and decentralized information exchange. As a matter of fact, digital encryption technologies are the core elements of blockchain technology, thereby drawing attention towards blockchain cryptography.
The assurance of security for user information and transaction data is a mandatory condition for encouraging the popularity of blockchain. So, what is the importance of cryptography in blockchain? The following discussion attempts to reflect on the basics of cryptography and blockchain alongside different types of cryptography implemented in blockchain networks.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
The Significance of Security for Blockchain
Before we dive right into understanding the role of cryptography in blockchain, let us reflect briefly on the blockchain itself. It basically refers to a distributed database that offers the features of decentralization, security, traceability, reliability, and immutability. Blockchain takes away the need for traditional approaches for maintaining central nodes and introduces the new approach for mutual maintenance of nodes by multiple users.
As a result, it can entrust information supervision to multiple parties and ensure desired levels of credibility and data integrity. Another important aspect pertaining to blockchain refers to the three distinct types of blockchain platforms. The types of blockchain platforms include public chain, private chain, and alliance chain. All the nodes in a public chain could easily participate or withdraw from the blockchain according to their preferences.
On the other hand, private blockchains impose specific conditions to determine the eligibility of the participating nodes. The alliance chain operates under the joint management of different participating organizations. Over the years, blockchain has been largely associated with the financial industry. However, it has showcased the promising potential for adding value to different sectors alongside reshaping the fundamental tenets of our society.
So, what is the relationship between blockchain and cryptography? The blockchain serves as a representative of distributed databases by storing all the transaction information of users on the blockchain. Therefore, it is reasonable to identify a profoundly higher demand for security performance in the blockchain.
Since blockchain operates with a decentralized, peer-to-peer network model, there is no single node, and nodes don’t have to trust one another. So, blockchain must also ensure appropriate safeguards for transaction information on unsecured channels while maintaining transaction integrity. Therefore, cryptography becomes an essential requirement for blockchain to safeguard user transaction information and privacy alongside ensuring data consistency.
Also Read: Blockchain Security: Premium Protection For Enterprises
What Does Cryptography Bring for Blockchain?
Now it is important to get a detailed impression of cryptography before taking an overview of blockchain cryptography explained properly. What is cryptography? Crypto basically refers to secrets in the literal sense. Therefore, cryptography technologies are aimed at ensuring complete or pseudo-anonymity.
The primary applications of cryptography primarily focus on ensuring the security of participants and transactions, safeguards against double-spending, and lack of influence of central authorities on operations. Cryptography finds applications across a wide range of purposes. In some cases, it helps in securing different transactions happening on a network. On the other hand, it also finds applications in verifying the transfer of digital tokens and assets.
Blockchain applications leverage the concept of real-world signatures by leveraging cryptography techniques along with encryption keys. Cryptography methods utilize advanced mathematical codes for the storage and transmission of data values in secure formats. As a result, it ensures that only the individuals for whom the transaction or data is intended can obtain, read and process the transaction or data and verify the authenticity of participants and the transaction.
Enroll Now: Enterprise Blockchains Fundamentals – Free Course
Understanding Blockchain Cryptography with Examples
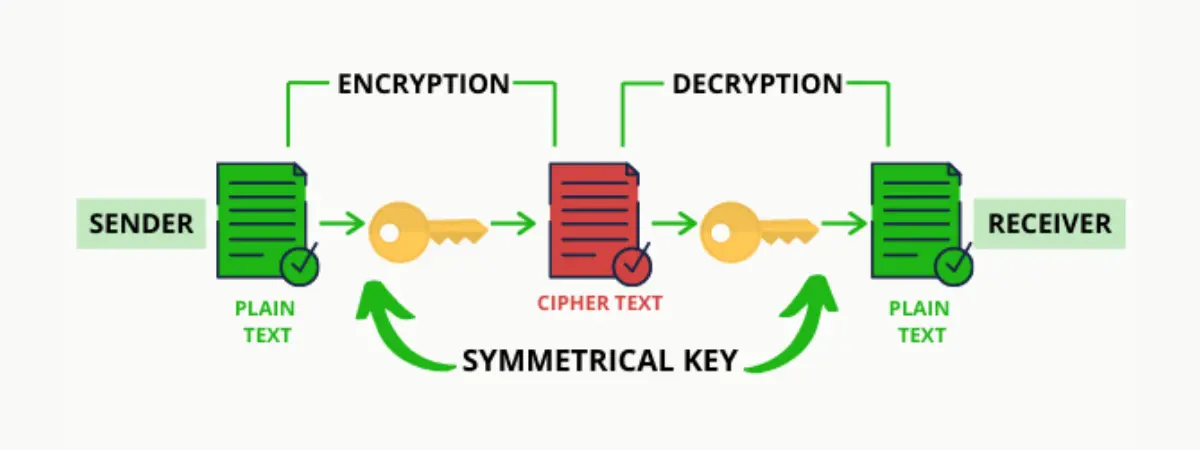
Blockchain cryptography is definitely a complicated topic. However, you can achieve a better and simpler understanding of cryptography by reflecting on the fundamentals of its working. Take the example of radio signals that help you listen to broadcasts on your vehicle’s radio. The broadcast is publicly available to everyone, and other people could also listen to the broadcast.
On the other hand, take the example of radio communications between two soldiers on a military mission. Such type of defense-level communications will be highly secure and encrypted, and only the intended participants can receive and know the information. You can find the applications of cryptography in blockchain in the exact same manner.
Basically, cryptography serves as a technique for the transmission of secure messages among two or more participants. The sender leverages a specific type of key and algorithm for encryption of a message before sending it to the receiver. Then, the receiver employs decryption for obtaining the original message. So, what is the important aspect in the operations of cryptography? The answer directly points out encryption keys.
Encryption keys ensure that unauthorized recipients or readers cannot read a message, data value, or transaction. They are the right tools for making sure that the intended recipients only are capable of reading and processing a specific message, data value, or transaction. Therefore, keys are able to bring ‘crypto’ traits to information.
The majority of blockchain applications don’t involve explicit use of sending secret, encrypted messages, especially in the public blockchain. On the other hand, a new generation of blockchain applications utilizes different variants of cryptography encryption for ensuring security and complete anonymity of transaction details. Many new tools related to applications of cryptography in blockchain have emerged over the years with diverse functionalities. Some notable examples of the tools include hashing and digital signatures .
With a basic outline of details in blockchain cryptography explained properly, it is evident that cryptography refers to the practice of creating protocols for preventing third parties from accessing and viewing data. The modern applications of cryptography bring a combination of different disciplines such as physics, math, computer science, engineering, and others.
However, the focus of applications of blockchain cryptography primarily emphasizes terms such as encryption, decryption, cipher, and keys. Readers must have already come to terms with the applications of encryption and decryption in cryptography. Cipher is the algorithm that helps in performing the processes of encryption and decryption, generally by following a series of well-defined steps.
Keys refer to the trivial amount of information required to obtain output from the cryptography algorithm. Now, let us take a look at digital signatures and hashing, the two components that establish the significant role of cryptography in the blockchain.
Want to become a Cryptocurrency expert? Enroll Now in Cryptocurrency Fundamentals Course
Implications of blockchain and cryptography with Digital Signatures
Digital signature basically refers to a mathematical approach for creating digital codes that are utilized for verifying whether digital messages and documents are legible or not. Public-key encryption is suitable for producing and substantiating the codes. In addition, attaching digital signatures to an electronically disseminated document ensures verification of specifications of the content and the sender.
Before diving further into the implications of blockchain and cryptography with digital signatures, let us reflect back on security fundamentals. It is important to address the requirements of four significant traits in the online transmission of valuable data. The four important traits include confidentiality, non-repudiation, authentication, and integrity.
Generally, encryption algorithms such as AES can address the need for confidentiality. However, digital signatures are preferable alternatives for addressing the requirement of the other three traits of non-repudiation, integrity, and authentication. The effectiveness of blockchain cryptography with digital signatures depends a lot on two prominent methods of encryption.
Also Read: Cryptographic Hashing: A Beginner’s Guide
Symmetric-Key Encryption
The first type of encryption refers to symmetric-key encryption. Symmetric-key encryption focuses on using similar keys for encryption as well as decryption of data. Most important of all, the symmetric-key encryption method is applicable in various information security use cases such as encryption of your hard drive or security of the connection to an HTTPS website. The use of a similar key for encryption and decryption creates issues in the safe transfer of the key between the receiver and the sender. Symmetric-key encryption is also referred to as secret-key cryptography.
Asymmetric-Key Encryption
The second encryption method that has a profound role in the applications of cryptography in the blockchain is asymmetric-key encryption. Asymmetric-key encryption is also known as public-key cryptography and involves the use of different keys for encryption and decryption processes.
The public key and private key can serve the roles of the encryption key and decryption key, respectively. Asymmetric-key cryptography algorithms generate the key-pair, and the public key is shared openly while the private key is maintained in secret. Public-key cryptography, as it is also called, can help two completely unknown parties for exchanging information securely.
Digital signatures leverage public-key cryptography and help individuals to prove ownership of their private keys. Interestingly, users don’t have to reveal their private keys to the other parties as they can prove it by decrypting messages. So, the applications of cryptography in blockchain with digital signatures focus on the transaction process for ownership verification.
Also Check: How Does Blockchain Use Public Key Cryptography?
Use of Cryptographic Hashing in Blockchain Cryptography
The use of cryptographic hashing is also one of the notable highlights in blockchain cryptography explained properly. As a matter of fact, cryptographic hashing presents a basic component of blockchain technology. Hashing enables immutability in blockchain, the most significant feature in the blockchain. The encryption through cryptographic hashing does not involve the use of keys.
On the contrary, hashing in cryptographic leverages a cipher or an algorithm for obtaining a hash value of a particular length from the input. Hashing involves taking a string of any length as input and producing an output with a fixed length. The most common applications of hashing in blockchain are evident in the use of the SHA-256 cryptographic hash function.
Cryptographic hash functions offer various unique traits which establish their productivity for blockchain cryptography. Here is an outline of the characteristics that make cryptographic hash functions suitable for blockchain use cases.
- Cryptographic hash functions are deterministic. Therefore, no matter how many times you enter a specific input, the hash function delivers the output of the same length. So, whether you enter a string with 3 characters or 200 characters, you would receive the output of the same length, i.e., 32 characters in a fixed string with a combination of numbers and letters.
- The second important trait that is evident in the case of cryptographic hash functions refers to the uniqueness of output. You don’t have to worry about two different inputs having the same output with cryptographic hash functions. Therefore, they can also offer unique functionalities for avoiding any collisions.
- Cryptographic hash functions are also associated profoundly with the trait of irreversibility. It is basically impossible to derive the original input from the output by using existing technology and techniques.
- Another profound characteristic that establishes the significance of hash functions in blockchain and cryptography is the faster computation of hashes. Hash functions can generate outputs faster, thereby ensuring better prospects for faster transaction completion.
- The avalanche effect is also a prominent highlight in the traits of cryptographic hash algorithms. The avalanche effect basically implies that a small change in the input results could lead to a completely different output.
SHA or Secure Hash Algorithm is the most widely used cryptographic hash function with many variants such as SHA1, SHA256, MD5, and SHA512 being used commonly. Every cryptographic hash function has its unique function as follows,
- MD5 or the Message-Digest algorithm helps in generating a 128-bit hash value
- SHA1 is the upgraded version of SHA tailored by NIST and published in accordance with FIPS or Federal Information Processing Standard
- SHA256 function involves hash value computing with 32-bit words and message digest amounts to 256 bits
- SHA512 function involves hash value computing with 64-bit words and message digest amounts to 512 bits
Therefore, it is clearly evident that cryptographic hash functions offer unique benefits of mathematics with various appealing properties. So, how are the properties of cryptographic hash algorithms relevant for the role of cryptography in blockchain? Basically, the characteristics of hash functions ensure the following benefits,
- Access to proof of ownership of specific information without revealing the information
- Prevention of unauthorized modifications in transactions
- Verification of transaction confirmation without complete knowledge of the block
- Reduction of transaction bandwidth
- Development of cryptographic puzzles for transactions
Enroll Now: Certified Enterprise Blockchain Professional (CEBP) Course
Final Words
Now that you know about the significance of blockchain cryptography, it is important to understand the scope of a career in blockchain security. The basic tenets of cryptography align perfectly with the fundamental characteristics of blockchain technology. While digital signatures are trustworthy tools for encryption of blockchain network communications, cryptographic hashing has a better potential for cryptography.
Cryptographic hash functions take away the need to depend on keys like in public-key cryptography. You can learn more about cryptography and its applications in blockchain with the right resources at your disposal. Check out the Certified Blockchain Security Expert certification training course on 101 Blockchains right now!