Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Reviews
Hasib Anwar
- on August 21, 2018
Security Token: An Emerging Trend as ICO Alternative
The common investors were always afraid to invest in the blockchain technology. The reason is quite simple and understandable – volatility. Even some investors feel that the world of blockchain investment is too unpredictable and uncertain. The interesting part is – they are not entirely wrong! Maybe, that’s the main reason for the drastic decline in ICO investment in the last quarter of 2018. So, what could be the solution to this tricky problem? Well, there is a new solution on the horizon – Security Token.
The idea of the security token platform is fairly new. With the security commissions like the SEC being too concerned about recent incidents, we kind of predicted a more modern technology to come in the game. Basically, the security tokens sort out some of the fundamental problems of the traditional ICOs.
We are all well aware of the DAO incidents, and some other high-octane ICO fails. The investors have lost a lot due to the fraudulent ICOs. Now, SEC is being too strict about allowing the ICO. Gradually, the list of security tokens crypto, the issuance companies, and security exchanges came to being.
We believe the crypto security tokens will play a big role in the blockchain scenario and soon we will witness even positive gradients in the investments.
As the whole concept of the security token platform is quite new to the mass people, we thought to work on a definitive guide to help you to understand the entire concept.
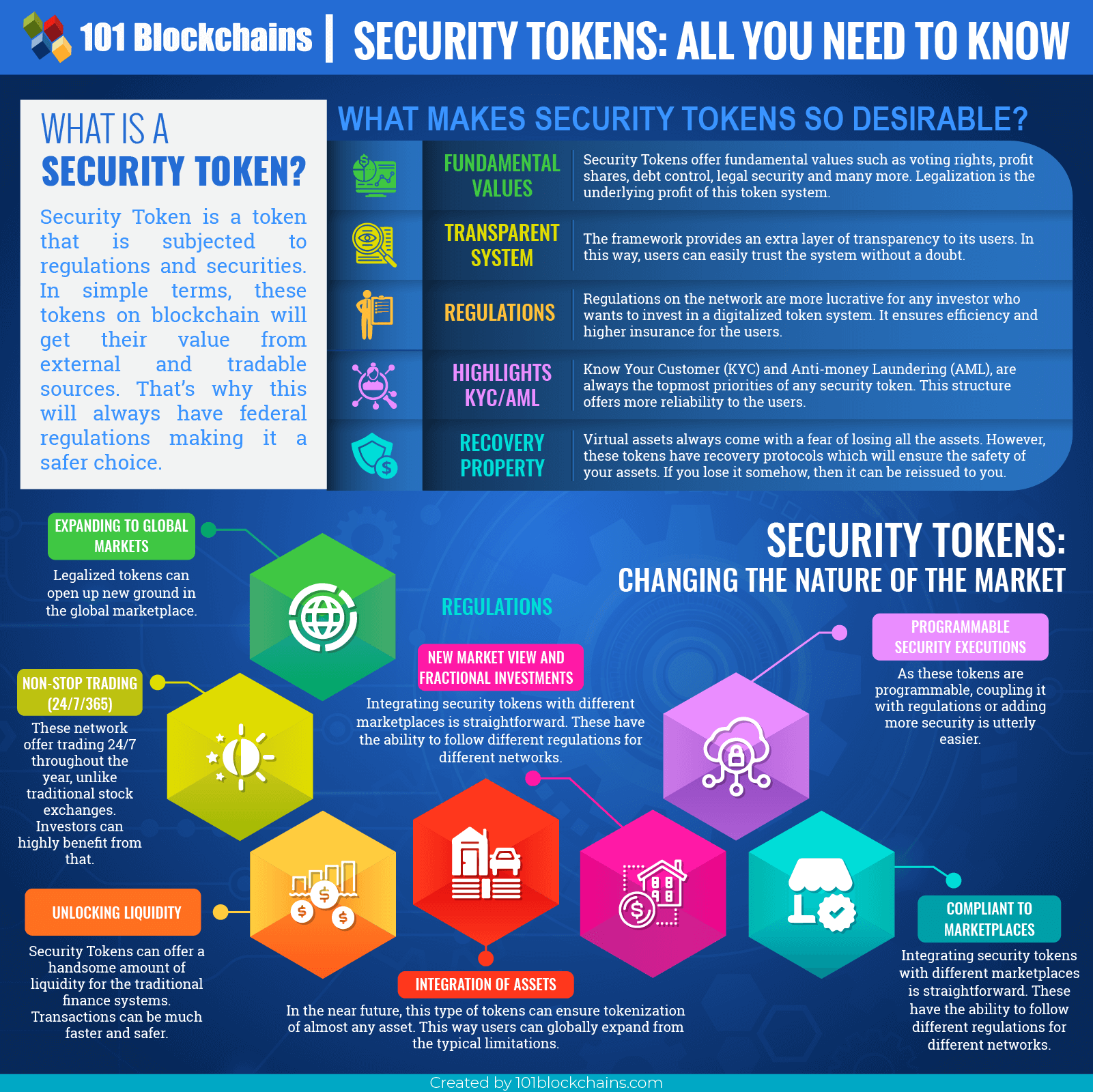
SECURITY TOKEN INFOGRAPHIC
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2018/08/Security_Tokens.png' alt='What is a Security Token?='0' /> </a>
The SEC vs. Blockchain
Before we move on to the list of security tokens crypto, let’s talk a little bit about what SEC is and about their duties. SEC also knows as the U.S. Securities and Exchange Commission is one of the independent agency working under United States federal government.
Their primary responsibilities include – to enforce federated laws and securities, industrial security regulations, propose different security rules, maintain stock exchanges and other organizations. They also offer electronic securities.
However, their main concern is to provide protection for investors, maintain an efficient and fair market.
With the integration of blockchain technology and token economy everywhere it’s a wonder why the SECs haven’t classed these tokens as securities before. Back in 2016, the SEC didn‘t seem to bother looking into ICOs and enforcing regulations.
However, that scenario changed entirely with the collapse of Ethereum later that year.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
The Fall of DAO
DAO was on a roll that time being the most crowdfunded project in blockchain history. They were breaking records almost every month, and they raised $150m, which is quite surprising. It’s because many were concerned with the system and thought it might be hackable. But still, investors poured their money into their ICO one after another.
At that time, the founders reassured the critics several times saying, they have everything under control and every fund raised is extremely safe. Unfortunately, the hacker found an algorithmic loophole and stole $50m of the invested money, and Ethereum took a big hit dropping to 50%.
A lot of investors were utterly disappointed and contacted the SEC. It was then when SEC first started to concern themselves with crypto and blockchain. They published a report for the application of cryptocurrencies with the fundamental principles under the new paradigm. The new standard defined them as digital organizations who utilize any kind of blockchain technology or distributed ledger for raising money or capital.
With this new law in force, cryptocurrencies would no longer be the unregulated digital currencies as they were before. If they want to exist, they would need to be defined as a security token platform. After the DAO incident, it was listed as a security token platform really fast. So, we might see a lot of new players with the list of security tokens crypto in the future.
Excited to develop fluent knowledge of the DAO ecosystem? Enroll Now in DAO Fundamentals Course!
How Can Regulations Effect Crypto?
After the SEC got involved, many of the ICOs (Initial Coin Offerings) are trying their best not to be associated with securities. What more is that, you’ll find another type of businesses growing that will tell you how to avoid being security and keep it that way.
But why are companies so desperately trying to avoid being a security token platform? Can restrictions really affect crypto in a bad way?
Well, some of the possible reasons may be the restrictions and rules of the SEC. If a regular token becomes a security token platform then by default, the company would have to deal with all rules. It also covers paying fees to compensate investors if things don’t turn out as they should.
Many companies try to evade it for this reason – to avoid any legal consequences. And in other cases, the issue is a bit high. They despise government involvement. This is one of the significant issues of regulation being with crypto.
The nature of cryptocurrencies demands a decentralized platform without any involvement from the government. But if the SEC gets involved certain decentralization won’t be possible, and it would go against the central philosophy of the blockchain.
The blockchain network has somewhat a wild market nature, and many adaptable investors can make a whole deal of money in a short amount of time. That’s why this type of investors are trying to keep the network that way so that they can keep profiting at any means.
Not Every Token Can be a Security
On the other hand, the SEC defines the security tokens a bit differently. As every token comes with a different nature, not all the token is capable of going side by side with the rules. For this, many tokens can never be defined as security tokens.
The tactical difference between these two rivals is the main reason why cryptos aren’t so fascinated with the regulations.
Let’s take bitcoin for example. Bitcoin doesn’t come with a development team and nor does it offer investors any promises of profit. On the other hand, Ethereum is far more complicated. However, it does have a utility token. But the holders of Ethereum aren’t actually expecting anything from the team. They don’t hope for a profit from the development group, and people are okay with it, then it should be kept like that.
For other tokens, the outcomes are kind of confusing. What if, a new cloud storage platform provides an ICO with a promise to share the profits among the investors and also provide them with a storage space? Will space be included in the utility or the benefit they promised? How would they differentiate between these two facilities?
So, as far as it goes, the situation is still quite complicated, and we would have to pay as much as close attention to the SEC and the outcome. However, things are starting to change, and the market is shifting towards security token platform rather than sticking with regular ICOs. Let’s see what the statistics tell us here.
Want to become a bitcoin expert? Enroll Now in Getting Started with Bitcoin Technology Course
Is Security Token Offering Replacing ICOs? – The Statistics
Let me start by going back where the first craze for ICO started. It started in May 2017 where ICOs raised about $200M, and it kept growing and growing. During the next two months, ICOs raised more than double the amount – $650M! However, in August, the marketplace came a bit down. But after August, it started growing again, and by December it raised over $1.7B.
During the first quarter of 2018, the ICOs raised about $7B, and the hype was super intense. However, in the following two quarters, the capitals took a huge hit and had been falling since. But still it managed to raise money, and the total amount concludes to $12.3B.
So, even though the ICOs did raise $5.6M in 2017, the craze took them to a different height in 2018. If we calculate the average capital for every token, we’ll get $29.7M.
But in 2018, almost 58% of the token crowdfunding failed, and only 42% managed to raise any money.
So, Why did the ICOs Fail or Started to Lose All Interest?
Well, there are some several issues why they failed. The main issue has to be the lack of product value. Yes, there were a lot of exciting products introduced in each token sale; however, only a few could maintain what they offered to their investors.
Secondly, most of the ICOs didn’t spend much for their marketing campaigns, and lack of it doomed their product in the end.
Another major issue is the rising scam ICOs. There have been several reports of ICO scams throughout the ICO craze, and many investors lost their money as ICOs don’t provide any legal backups for them. On the other hand, many investors were unsure of the newcomer or non-experienced development team to invest in their token sale.
As a result, the SEC stepped in and took control of the situation. The reassurance of the regulations and safety measures attracted the investors and the list of security tokens crypto started to gain popularity.
So, at the end of 2018, ICO is losing its audiences, where on the other hand, the security token platform is gaining them.
What is a Security Token?
Security Token is a token that is subjected to regulations and securities. In simple terms, these tokens on blockchain will get their value from external and tradable sources. That’s why these will always have federal regulations making it a safer choice.
From another point of view, the security token is one kind of tradable assets such as shares, bonds, notes, voting rights, options, debentures, and warrants. If you think about stocks, you would be able to get the idea more clearly.
For owning shares or stocks, you would own a portion of a company without actually taking real-life possession from it.
Many companies and government already use this method to raise money from the different types of investors to improve or fuel the projects. But what do the investors get regarding that? They will get a promise of interest or share on the company’s profit-making in any type of form.
When you are dealing with these scenarios in a cryptographic manner, it’s then known as the security token.
Want to become a Cryptocurrency expert? Enroll Now in Cryptocurrency Fundamentals Course
Making Things Easier
Mainly, compared to typical ICOs or utility tokens here the investors will always have a sure promise of profit. Whereas for ICOs the profit is a gamble of sorts. This security token will invest in any type of asset or token to provide the offered profits. And this takes care of the matter of the security token liquidity.
Back in the old days, where people used to get paper backups for their shares or bonds, the liquidity becomes a huge concern, but now with the integration of cryptography in the matter, you won’t have to deal with the problem.
Just imagine a scenario, where you are getting paid for meeting any specific rules or conditions automatically using the smart contracts in the blockchain platform. Wouldn’t that make things much easier?
So, all of the programming ability of this security token ecosystem can swift up the process and can transition from a typical form to many more. Just as the company will grow, so will your profit and the features will increase for every token.
If one of the companies can’t provide or fails to provide the features they claimed to give you; they will have to face legal issues. So, you won’t be kept hanging out in the air.
Want to know everything about blockchain security? Read this article: Blockchain Security: Premium Protection For Enterprises
What’s The Difference?
In practical cases, you can compare it to ICOs. Like the ICOs these also come with investors. But the similarities kind of ends here. For an ICO, if you invest in it, you could expect to benefit from the token success rate or to utilize the platform itself freely. For ICO offering, you would need the token to maintain or use the network correctly. However, the platform itself could be successful, and the price of the tokens could rise. But that’s a gamble.
On the other hand, investors in security token ecosystem will invest in expecting to receive in future rights or cash or bonds that are directly linked to the tokens.
Additionally, the security token ecosystem is compatible with the laws and regulations, so investors from all around the globe can participate if they manage to follow the rules. This can open up a lot of options where laws are relatively strict like the U.S.A.
Moreover, with the help of security token ecosystem, all companies can create blacklists and whitelists. These lists comply with the AML (Anti-money Laundering), and KYC (Know Your Customer) reports. The companies will operate more transparently and will be more attentive to the raised funds and company failures.
So, where ICOs don’t have any security for your funds, in security token your funds are safer than ever.
How Does It Work?
Okay, now that you know all about what security token ecosystem is, let’s take a closer look at how it works. It follows the same rule as all the tokenization company follows. First, an issuer will issue a security token that will represent any portion or share of any enterprises. After that, the issuer will create a whitelist, and in that list, it will have the wallet addresses of the investors who can participate in the token sale. Mainly the wallet address is usually Ethereum’s for now.
The listed investors in the whitelist would have to prove their compliant with the rules and regulations set by the issuer. The laws vary with each security token ecosystem, so you might see a lot of variations if you invest in a lot of top security tokens.
This has a close connection to AML and KYC regulations along with proving your identification with credible sources. Not that every security token ICO is backed by hundreds of regulations. However, the issuer could comply it with a vast number to filter out the investors more easily.
Maybe for some cases, you would need to have certain backgrounds or career position to participate.
Want to learn the fundamentals of tokenization? Enroll Now: Tokenization Fundamentals Course
Outsourcing for Investors
The issuer could also outsource the investors to make the final call. They can do it by using third-party services like centralized exchanges to know what type of investors typically invest in companies. These lists then become the liquidity group. Here, everyone on the list will be able to trade the security token with each other if they want.
But what happens when someone else tries to enter the whitelist when he didn’t make the first list?
Well, in that case, the issuer will help you out. The company can allow the third party to follow up the KYC/AML rule and add up new investors in the whitelist simultaneously. In this way, the third party won’t have to go to the issuer every time someone wants to invest in a security token.
In the long run, this scheme really pumps up the liquidity of the system making them more valuable in the future.
There are no restrictions on how you can trade your security token, but you do have to be on the whitelist. Now many exchanges such as Open Finance or tZERO will allow you to trade the securities on their platform just like typical crypto exchanges.
If the issuer is relatively new and doesn’t know how to start a security token sale, then there are companies to help them out. Some of the networks such as Harbor network or Polymath network are extremely popular. These companies help the issuer companies to tokenize the security assets. They take the real-life values and turns them into a programmable token in the blockchain.
Can’t Be Hacked
Another fun fact about the security token ecosystem is that they aren’t some instruments that someone could easily steal from you. In typical cases, if someone on blockchain gets your private key, he/she can spend your cryptocurrencies without you doing anything about it.
Kind of like you lost a $100 then someone could just pick it up and spend it. You won’t actually be able to do anything about it, will you? But for security, they can’t just easily transfer your token on their wallet to use it.
They would also have to comply with the KYC/AML to be whitelisted. So, if someone does break in and hack his/her way to your wallet, you would be able to trace it back to their whitelisted wallet and then take legal actions against them.
So, in the end, the list of security tokens crypto does provide a lot of securities just like their name.
STO vs. ICO: How to Determine If a Token Is a Security?
To invest in security, you would need to know what makes it different from ICO. If you want to know whether a token is a security concerning STO vs. ICO debate you would need to know more about the Howey Test.
So, let’s see what the Howey Test is and how this test will allow you to judge the token.
Not sure what is the difference between STO and ICO? Read this article to know more: STO Vs ICO: The Difference Between The Two
The Howey Test
Let me start by saying how the Howey test first came to be. Back in 1946, the Supreme Court had to face strange circumstances for a case. This case was between the Howey vs. SEC, and it was the time where the foundation of the Howey Test came to be.
The case resulted in an outcome where the Supreme Court ruled out a test. In this test, one can determine whether a particular project would be considered an investment agreement or not.
In short, the story is kind of like this; two Florida-based corporate defendants provided real estate shares in the land for citrus groves. The buyers offered the investors a chance to own a portion of the land from them. And they would maintain the property and harvest and market the citrus and give a profit from that.
Most of the investors weren’t farmers, so they didn’t actually have any agricultural knowledge. But the proposal was good enough to make them invest in that.
However, the SEC tried to make the defendants’ project look illegal stating that they didn’t provide any security backups. After that, they were sued for that.
The SEC believed the defendants didn’t register their project as a security statement, so they broke the law. However, after investigation and leasing documents, the Supreme Court found out that the project was indeed security and they didn’t break any law.
A New Proposal
To make sure, this situation doesn’t occur again; the Court issued a test to determine whether any project or new business falls under the security registration requirement.
So, to know whether it’s an investment contract or not, it would have to fulfill three main criteria’s –
- You would have to invest with money.
- The investment will take place in only a common enterprise and not multiple enterprises.
- All investors will profit from the outcomes of the project or company.
Here “common enterprise” could be many things. But most of the federal courts define it as a space in the enterprise where the investors can pool all their money at once and invest in the project directly.
After many years, the “money” term was more expanded, and people now can invest with assets or other methods.
Another aspect is that, whether the investors control the profit or not. If the control isn’t on the hands of the investors, then the project is already a security.
So, here, the digital tokens will be security if the token follows the three rules of the Howey test. If it fails to maintain any one of the rules, then it would not be a security token ICO.
Regulations of Security Tokens
There are some certain regulations that every security token ecosystem needs to follow to stay included in the genre. The federal rules will start from the very first day; however, it could vary from country to country, according to their federal laws.
In the U.S.A, a security token need to follow some certain rules –
Regulation D
This regulation will allow a company to provide particular offerings but they have to file a “Form D” after all of their security gets sold. The company or individual who would offer the security token ICO could ask the investors to invest in them if the company is compliant with the Section 506C.
But what is the section 506C?
The 506C section will require verification of all the investors and offer itself during the solicitation. It means that every statement provided by the company is valid and there isn’t any misleading information on that.
Regulation A+
This type of regulation will allow the company to provide SEC-approved security for non-verified investors. But they would have to solicitant through general channels and can allow each investor to invest up to $50M.
However, for this regulation, the issuance can take a lot more time than others, and for this reason, it’s more expensive.
Regulation S
This type of regulation occurs when a company executes their security token offering list in a different country and not the US. That’s why it won’t be exposed to the registration requirement that falls under section 5 of the 1993 act. However, the company has to still follow the rules of the country where they are executing their security token ICO sale.
Note: I’ll have to say, the above regulations are just interpretation. You should not consider this as legal advice. So, always consult with your lawyer to investigate it more before you start a security token offering list.
Curious to learn about blockchain implementation and strategy for managing your blockchain projects? Enroll Now in Blockchain Technology – Implementation And Strategy Course!
What Makes Security Tokens So Desirable?
-
Fundamental Values
The list of security tokens crypto offers fundamental values such as voting rights, profit shares, debt control, legal security and many more. Legalization is the main fundamental profit of this token system.
You won’t find this in typical utility tokens. In Utility token, you could only have minimal values tied to your tokens such as, with your token you could have access to the service or product. But with the security token, you would have many values that are directly tied to the security token you are holding. And you would get every benefit from it.
Security token will provide a legal right for you, through that you will own an intrinsic value of the issuance company. These will have higher terms of value and thus would reduce the risk massively. You can calculate the fundamental value through various means.
You can use the discounted cash flow, residual income architecture and divided discount method to calculate it. In simple terms, a security token with the fundamental value already has a value from the day you invested in it.
It may later increase or remain the same, but you would get the advantages of the security token right from the start.
Plus, the security token is a valid form of investment as they have more simple and basic architecture. For example, tZERO provides 10% of the profit to its investors, and you would get it right from the start.
Want to become a Cryptocurrency expert? Enroll Now in Cryptocurrency Fundamentals Course
-
Transparent System
The framework provides an extra layer of transparency to its users. In this way, users can easily trust the system without a doubt.
The security token will allow all the investors to look into the credibility of their offerings. Before investing the investors can gather information without anything to hide. So, all the list of security tokens crypto issued, offered and distributed will be open for everyone to examine.
The main priorities of a security token are to follow three basic criteria –
A healthy way of forming the capital.
Shield investors from making errors and protect them from external fraud activities.
Hiring a proper channel to maintain fairness in the system and ensure order in the marketplace.
The architecture of the security token ICO is visible for everyone; however, the network itself is immutable. So, even though it’s super transparent, no can just hack into the system with that information. That’s why the security token ICO can maintain all three aims and offer a better landscape for the investors.
-
Regulations
Regulations on the network are more lucrative for any investors who want to invest in the digitalized token system. It ensures efficiency and higher insurance for the users.
The list of security tokens crypto that is more with the agreement with the law is gaining much more popularity among sophisticated investors. These have more efficiency, provide a steady pace and transparency in comparison to typical cryptocurrencies.
ICOs did dominate the 2017 and most of 2018. But after the SEC came in the scene, they declared many ICO as security tokens. However, the classification doomed the ICO, as most of the companies are securities but haven’t registered or can’t maintain the regulations that come with it.
That’s why the SEC took many legal actions against these ICOs, and the decrease in ICO sell started to happen. So, to not face any problems such as this, the security token would have to register from the start.
If they have a head start from before, it becomes much easier to draw the line of law and blockchain together. By doing so, many security tokens will have an advantage over other companies that came after them.
Learn the fundamentals, working principle and the future prospects of cryptocurrencies from the E-book: AN INTRODUCTION TO CRYPTOCURRENCY FUNDAMENTALS
-
Recovery Property
Virtual assets always come with a fear of losing all the assets. However, these tokens have recovery protocols which will ensure the safety of your assets. If you lose it somehow, then it can be reissued to you.
I think we all know how every investor of the digital assets fears the loss of their virtual currency. I mean, losing it is much easier than physical assets. However, with the rise of cryptocurrencies, the lack of recovery protocols is one of the main drawbacks of this new marketplace.
On the other hand, if a security token is properly constructed, you would be able to enjoy the reissuance feature. However, to have this feature, you would have to provide evidence of you actually having the security token from the start.
There could be several ways to verify or provide evidence. It’s mostly outlined form the company from beforehand.
-
Highlights KYC/AML
Know Your Customer (KYC) and anti-money laundering (AML) are always the tops priority of any top security tokens. This structure offers more reliability to the users.
These two protocols are at the core of the mainframe of the top security tokens. However, the constant requirement of auditing and providing reports can become a burden; still, the security token has to deal with this.
It’s quite easy to integrate AML in typical exchanges where you are dealing with the normal banking system. But when it comes to the distributed ledger, it becomes much more complex. As the addresses are anonymous investors, auditing them is a bit of a challenge.
But in the security token, the company would be able to track and monitor transaction to ensure that everyone is following the rules. It also allows the creators to offer better values to their customers based on the output.
The mainframe also doesn’t allow anyone to trade outside the whitelisted addresses. This offers a better efficiency for the law enforcement as any investors can directly take legal action against another address if he/she tries to tamper with other accounts.
Want to get an in-depth understanding of crypto fundamentals, trading and investing strategies? Join the Standard & Premium Plans and get free access to Crypto Fundamentals, Trading And Investing Course.
Security Tokens: Changing the Nature of the Market
-
Unlocking Liquidity
Top security tokens can offer a handsome amount of liquidity for the traditional finance systems.
Back in the old days, typical banking systems took a hefty amount of time to process a transaction. But the process did speed up over the years; still, it needs more fuel. Before it took five days after the trading date and now it takes only two days.
But with the weekends, many aren’t able to just instantly send money using that in times of need. With this much transaction happening every day, the process of clearing every payment each day is becoming more robust. And this type of scene is revoking the liquidity of the finance sectors.
On the other hand, if you can get rid of the usual boundaries of the typical banking system, then you will easily be able to speed up the process. Just imagine a scenario where you will be able to instantly send money to another without waiting for any processing time.
Examples of security tokens 2018 can do that easily, and transactions can be much faster and safer. That’s why security token crypto can shape up the typical financial sectors and mold it into something new.
-
Expanding to Global Markets
Legalized tokens can open up new ground in the global marketplace. This usually depends on the different types of security token or how the company allows the users to invest in it. For example, a person living in the U.S.A could buy ownership of a small barista in China or other countries. And this can go vise-versa.
But just how much far can the global market actually provide output? There are some certain cases where the stablecoin token attracted investors from over 50 countries and more. So, this could be the best option for other countries to get ahold of a share that is really hard to understand.
This unites the whole world together instead of differentiating them and can grow globally more efficiently.
-
Non-stop Trading (24/7/365)
In typical traditional exchanges, you will find them working for 6-7 hours a day and only be open on weekdays. This is somewhat disruptive for usual investors as they can’t check up on their stocks or sell them when the prices get down.
However, security token does offer trading 24/7 throughout the year, unlike traditional stock exchanges. Investors can highly benefit from that. In this way, no companies can plot against the investors or use it to make their prices go up.
Everyone will be able to trade and monitor their security tokens easily every day and every second.
-
Integration of Assets
In the near future, this type of tokens can ensure tokenization of almost any asset. Top security tokens will open up a new type of marketplace in the future. With the help of it, everything from our daily life can be tokenized. Just by using this, users can make assets from their own possessions and offer profit or other benefits to the investors or shareholders.
This way users globally will expand from the typical limitations. It could mean that the ecosystem may shift entirely based on the security token. An investor might be able to invest in different top security tokens and keep them in the same wallet address together.
Not only it will be much easier to manage them simultaneously, but it will surely be a lot of automated processes. By doing this, the global liquidity pool would gradually increase.
-
Compliant to Marketplaces
Sometimes it becomes a hurdle for typical assets to be included in every market scenario. Different marketplaces come with their own set of rules and regulations. And as typical legal assets have to be integrated with every law, it becomes quite complicated.
With loads of paperwork and changing asset characteristics to act in a certain way requires more investment than profit. However, it’s very easy to integrate security tokens with different marketplaces. These have the ability to follow different regulations for different networks.
As you can just program a security token ICO to act a certain way, it takes less time and minimal paperwork. Many believe that top security tokens would take over the typical securities in the near future.
-
Programmable Security Executions
As these tokens are programmable, coupling it with regulations or adding more security is utterly easier.
Offering Dividends
Offering dividends in the back days were a bit of typical and kind of unfair. Due to the lack of paperwork or automation process, many companies won’t give any extra dividend to individuals who kept their shares for a very long time.
For example, imagine you and Mike own the same shares. However, you owned it from the last three years, and Mike just started investing in them a couple of days ago. Now if the company offers a dividend, it won’t be fair if both you and Mike get the same thing, right?
As security tokens can be programmed to act accordingly, the company could use an algorithm to track loyal investors and offer them a better solution.
If investors get more profit for holding the shares for too long then, people would be more eager to invest in those companies.
Voting Rights
This is kind of similar to how the security token ICO can program the dividends to distribute the profit more efficiently. But instead of dividends, they can use voting rights to add more variability in the profit offering. If you have owned the shares for three years, you would obviously get any kind of voting or governance right.
Although the theme isn’t new, many blockchain companies already provide this feature. However, with the help of the tokenized securities you can easily streamline this process. This also ensures a better architectural governmental system within the network.
Unique Privileges
Imagine you getting a special promo for the company’s products or special discounts for holding their shares for a very long time. If the company offers more discount for the greater amount of time, investors will be more eager to hold their ground and raise the prices.
You can do it by integrating the identification method, and this could further be the new affiliate scenario. However, many companies already do this to increase their popularity and to tell the truth it works.
-
New Market View and Fractional Investments
A more exciting way tokenized securities can affect the marketplace. It can introduce fractional ownership of any product. Just imagine that you want to invest in real estate, but the prices are too high for you to invest in. You also don’t want to take a massive risk by spending so much money on one property. To tell the truth, the whole concept of investing is a gamble.
So, what can you do in that aspect? Well, tokenized securities can allow a user to own a fraction of an asset. This opens up a new vision for investors. So, when it comes to a specific property, you can just buy a small portion which you can afford along with other people.
So, when the property is sold, and you get the profit, it will get divided up automatically based on your ownership status. You can book or buy any product at any time. You can invest in any kind of security token.
The company can execute the automation process through the help of smart contracts, and everyone will get their fair share of the profit. No one has to deal with the paperwork or to look for buyers or to show people the house to sell it. It’s super easy now.
Not sure how to build your career in enterprise blockchains? Enroll Now in How to Build Your Career in Enterprise Blockchains Course
Security Token Issuance Platforms
-
Polymath
It’s a wonderful blockchain platform that offers issuance services of any tokenized securities along with the integration of the SEC regulations. Meaning, if you want to launch your very own security token, Polymath network will surely help you out in issuing your token and complying them with regulations from beforehand.
The protocol of Polymath network will streamline every process of launching any financial product on the blockchain platform with embedded financial statements.
Polymath network also offers a platform investors can get authenticated for trading security token, connect your company with legal advisors and give you access to developer marketplace. You would have to use their token “Poly” which is an ERC20 token to use their platform.
Polymath network is utterly popular among new issuers, and they have worked with different security tokens so far.
A lot of blockchain aspirants have confusion in ERC20 and if you’re also one among them, then you must read this article- What Is ERC20? Beginner’s Guide
-
Harbor
This is another platform for companies that want to transition into the tokenized securities line without any hassles. Harbor is one of the popular issuance platforms nowadays, and many companies are using their services to start their very own security token.
This complaint will ensure that each company that is migrating their assets into the blockchain framework gets complaint with proper regulations.
The platform provides access to ICO using Reg D to comply the token sale. Their other features include standard protocols such as, reports, audits, certification, tax rules, and KYC/AML integration with every new token that uses their platform. So, Harbor can be a wonderful solution for companies that want to start their tokenized securities but require help in that regard.
-
Securitize
This is another one of the popular choices nowadays for issuing security token. They provide a cloud solution of regulatory compliant. However, they are most expert in tokenizing different funds, companies and other entities that want to start their security token project out of scratch.
Securitize offer a wide range of services for the issuer company. First of all, they would make sure that the issuer and the development team is fully in sync with the regulations. They would also streamline the whitelisting processes by using KYC/AML authentication. Other than these two, they can also customize smart contracts to match with the scheme of the issuer.
Securitize already provided their services to a lot of popular companies that are running their security token offering list scheme up to $500M. The projects are – Lottery.com, 22X Fund and many more.
-
Swarm Fund
Using the SR20 protocol, Swarm Fund is another top issuance platforms now on the market. This is a cryptographic protocol standard for only security tokens and allows this company to tokenize any real-life asset in the blockchain.
After tokenizing the real-life asset, the security token offering list becomes a governed, managed and trading token on the swarm system. You can get your hands on the SR20 token using other cryptocurrencies such as Bitcoin, Ethereum instead of money. For investors who will get the SR20 token can have additional governmental rights, can trade the security token legally, and will have profits that come from the token itself.
The best part about this issuance platform is that they cover a wide range of areas such as real estate, agriculture, tech niche, hedge funds, renewable, impact investments and many more.
Top 4 Existing Tokenized Securities
In the dawn of top security tokens, at present, you’ll find a handful of issuer companies. There are other projects on the way, but they would require some time to get become the frontier of financial investments. Let’s see what the popular, exciting examples of security tokens 2018 are.
-
Blockchain Capital or BCap
This is the first company that introduced security tokens with the public offering for their investors. By their STO blockchain sale, they wanted to improve the typical scenario of the token sale. Instead of offering the same limited advantages, they wanted to offer the investors a secure way of investing in ownership.
This offer became the blueprint of today’s security token. BCap invested in other potential ICOs and only took investments from whitelisted investors. They grossed a capital of $10M within just six hours of release.
Every profit that comes from the company goes straight to their funds. From there the managers of the fun takes 2.5% for management and another 25% for a performance fee. The remaining profit gets distributed to all the STO blockchain holder.
To know more about Enterprise Bockchain, Enroll now in our Enterprise Blockchains Fundamentals
-
Science Blockchain
This is a slightly different type of security token issuer. Science Blockchain works kind of like an incubator for new blockchain investments and connects multiple blockchain projects together. They believe that blockchain is the future and they want to give people an option to profit from the stream of new tokens they would be introducing.
What they do is that they invest money in other blockchain companies and allow other investors to invest through them. This way the profit that the incubated companies produce will also benefit the investors.
They initially raised money for their project through security token offering list and offered an SCI token for the investors. The SCI token is directly linked to the profit of other companies working under them. From the profit, the investors will get up to 70%. But the best part is that this improves a lot of liquidity across platforms.
Their STO blockchain sale ended, and they raised $12.3M.
-
Lottery. com
If you love charities and want to invest in a humanization service, then Lottery.com will amaze you. This company is a mobile lottery game platform. The primary aim of the Lottery is to expand the transparency, break the global barrier, and provide more flexibility in the market.
However, they want to take a bit of a different road than others. The company is raising money to help in solving humanitarian needs. STO blockchain sale of this company is private and is rumored to have nine-figure range.
The vision of Lottery.com looks quite promising, and many investors are utterly excited about them. Other companies like Cashbet or Securitize is the partner for their STO and wants to help it to become more popular in the market.
They still have ongoing security token offering list sale, so the total amount raised is unclear for now.
-
SPiCE VC
Raising $40M from their STO blockchain sales, SPiCE VC is one of the leading forces in the STO blockchain niche. Venture Capitals is another popular form of real-life investments, and SPiCE VC tends to takes to the next level.
With the help of blockchain technology, they believe trillions of assets could be tokenized and used for the betterment of the financial sectors. Through SPiCE VC you will be able to invest in tokenized VC funds and enjoy the instant liquidity feature anytime.
Why are they popular? Well, in typical VC Fund, you’d have to wait for a minimum seven to twelve years for getting access to your funds. But in SPiCE VC you will immediately get the access and can trade it with other whitelisted investors.
Popular Security Token Exchanges and Upcoming STO Projects
Many people who are interested in blockchain must have come across Ethereum, Bitcoin, and many other renowned cryptocurrency alternatives. The most crucial aspect of all these technologies is decentralization, which drives the introduction of security token offerings. The concept of security token exchange emerged for addressing the complexities associated with the value of coins.
Initial Coin Offerings (ICOs) were associated with the main problem that the coins do not have fundamental value. With security token offerings, tokens are classified as digital representations of real assets like real estate or corporate equity. The STO is basically what stocks would look like in the blockchain world, and the security token exchange offers the platform for exchanging the stocks. Here are the top five security token exchanges you can use to trade in 2021.
tZERO is probably one of the most prominent names in the world of security token exchanges. The exchange has the most interesting feature in the form of its team that is the same team powering overstock.com. It is the brainchild of the CEO of overstock.com, Patrick Byrne. When the exchange was about to arrive in the market in late 2019, it was primarily associated with the exchange of tZERO tokens only.
The security token exchange basically offered a new opportunity for improving the growth of securities. In addition, it also has a promising potential for causing securities to take the place of utilities as preferred tokens. The most striking achievement of tZERO refers to their ability to successfully raise more than 300 million from their personal STO through the Start Engine platform alongside private capital funding by GSR Capital.
You could easily come across Polymath as one of the hottest STO projects in the blockchain ecosystem currently. It is considered as the parallel of Coinbase when it comes to asset tokenization. Just like Coinbase gained popularity among crypto beginners with an interactive arena for purchasing and selling digital assets, Polymath offers the same for asset tokenization.
The most crucial highlight of Polymath is the facility for simplification of the STO process. Polymath can guide business owners through the complete process of creating and issuing securities based on blockchain. Furthermore, it also supports issuing any entities that can manage their journey of tokenization. As a result, Polymath can ensure easier compliance with jurisdictional and legal regulations.
Capexmove is a trustworthy security token exchange for using debt through the blockchain. Capexmove can serve as a bond market for enabling businesses to issues debt. This clearly shows how STO platforms can provide the facility for executing financial functions which were accessible only to a few exclusive parties previously.
Generally, security token offerings are just like initial public offerings or IPOs. In some cases, they can help in obtaining capital in exchange for equity. The role of Capexmove in the business world is highly important, especially considering the facility of improved accessibility of lending markets. Furthermore, Capexmove also issues ERC-20 digital security tokens that enable trading in secondary markets.
The first decentralized security token trading platform in the US definitely deserves a prominent mention in the discussion on security token exchange. Investors looking for opportunities to trade in available security tokens can capitalize on Open Finance. Their partnership with the largest token issuers also works in their favor, with some tokens automatically pre-qualified for exchange listing.
BlockRules serves as the perfect intermediary for enabling the launch and management of client’s tokenization operations. In addition, the company could also offer the platform required for investors to purchase concerned security tokens. As a result, BlockRules helps in ensuring profound savings of time and resources for investors looking for opportunities in asset tokenization. Most important of all, investors can move from the usual ‘analog’ platforms with such as a viable alternative.
Not sure what Tokenization is all about, Read this article to gain a clear insight into Tokenization: How Tokenization Of Physical Assets Enables The Economy Of Everything?
Upcoming STO Projects
Reports suggest that around 15 countries have already been successful in defining security tokens in 2020. Furthermore, around 39 of the top 100 biggest banks worldwide are working on blockchain or security token applications. In addition, many international centralized exchanges have also popped up in recent times. Therefore, many upcoming STO projects also have the potential to make news. Here are some of the promising new projects among security token offerings you should watch out for.
- Cryptobuyer is one of the notable exchanges that can improve crypto mass adoption with the chance of offering POS solutions to merchants. The platform could provide access to the massive crypto ATM network for buying and selling.
- Thaler.One is another prominent contender among security token offerings that are working on the Ethereum blockchain. It allows investors to assume control or ownership of real estate assets all over the world.
- CityBlock Capital is capable of offering different funds all over the world with a profound reputation for promoting powerful partnerships. It focuses on starting different venture capital across different startups.
Limitations of Security Tokens: Is There Any?
With every new technology there comes some good sides and bad sides. The security token is opening a new door for investors, but doesn’t it have any limitations? Let’s see what limitations you might face while dealing with them.
-
Regulations Can Also Be A Curse:
Yes, they offer a lot of laws and regulations. These regulations do provide an added level of security for the investors but with regulations comes the limitations. Regulations can sometimes actually limit the proper output of these systems. Why? Well, it’s simply because blockchain and law don’t quite go well with each other.
With the introduction of regulations on blockchain platform, it kinds of getting rid of the decentralized aspect and are bound to the centralized law enforcement. That’s why many ICOs are trying to avoid being a security token.
-
Liquidity and Trading:
As you already know by now trading securities isn’t as flexible as typical cryptocurrencies. You would have to be whitelisted to trade the security token in both parties. For example, if you have “X” security token and want to trade it for “Y” security token. Both “X” and “Y” companies have to list you on their whitelist.
If you don’t have your name entered on the “Y” companies list, you won’t be able to trade “X” for that. This feature can limit the overall liquidity of the investors.
Curious to know the impact and in-depth understanding of crypto compliance in businesses? Join the Standard & Premium Plans and get free access to Crypto Compliance Fundamentals Course.
Conclusion
Security Token can be a new revolution for investment businesses. Yes, with the introduction of ICOs and blockchain people did get a lot of options to invest in. However, the increasing failure to provide the promise of profits is decreasing the popularity of ICOs.
I mean why you should invest in one if the company doesn’t provide any security for your invested money or is unable to give you the performance they thought could.
It’s still unclear how the SEC being in the mix, and the security token offerings could solve all the problem. This is still on the immature phase right now. However, everything so far does look a lot promising. So, we have to wait and see how it turns out.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!