Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Solidity & Smart Contracts
James Howell
- on October 27, 2022
A Guide to Smart Contract Security
Smart contracts are the core element fuelling the blockchain landscape, with many transaction use cases and various applications. You can find promising use cases of smart contracts in financial services, supply chain management, IoT networks, and even the music industry. The need for a smart contract security guide is evident with respect to the constantly growing magnitude of threats. Smart contracts are transparent and could lead to the exposure of undiscovered security vulnerabilities. Malicious agents can exploit such vulnerabilities to compromise customer data or cause significant loss in revenue.
Therefore, it is important to understand smart contract security and how it works alongside an outline of the important tools. The following discussion outlines a definition of smart contract security and its working alongside the notable issues associated with smart contract security.
Excited to learn about the critical vulnerabilities and security risks in smart contract development, Enroll now in the Smart Contracts Security Course!
Definition of Smart Contract Security
The outline of smart contract security best practices would be incomplete without a detailed understanding of smart contract security. Smart contracts are programs that run on a blockchain network such as Ethereum and can execute automatically upon satisfaction of predetermined conditions. The contracts serve as a helpful resource for storing or enabling transactions among different digital assets. Smart contracts could also help in speeding up the applications and adoption of blockchain technology. However, security vulnerabilities often result in stolen funds alongside a loss of trust or finances.
Smart contract security is the collective term for security principles and practices leveraged by exchanges, developers, and users during the creation of smart contracts and interactions with them. As a dynamic industry, blockchain and smart contract-based applications draw in billions of dollars. Malicious agents always look for opportunities to exploit the vulnerabilities in smart contracts to earn money.
Curious to understand the complete smart contract development lifecycle? Enroll Now in the Smart Contracts Development Course!
The complexity of Smart Contract Security
The outline of smart contract security issues could help you identify what you have to prepare against. However, you must learn about the existing state of smart contract security before diving into best practices for smart contract security. First, you must understand that smart contracts must be developed and deployed on a network using programming languages such as Vyper and Solidity. In addition, you would need an investment of ETH in the deployment process as gas fees. Apart from the operational challenges in deploying smart contracts, you must also look at the design challenges for smart contract security.
The need for smart contract security tools can also depend on the type of smart contracts. Some of the popular applications of smart contracts include DAOs or smart legal contracts. However, distributed or decentralized apps, also referred to as dApps, are the most noticeable application-based codes, working in combination with different smart contracts. The scope for smart contract security would also include Contracts of Applied Logic, or ALCs, developed on a decentralized network.
If the variations in types of smart contracts weren’t enough, smart contract security issues have exploded in recent times. The complexity of dealing with smart contract security would also account for the impact of recent smart contract security attacks. Here are some of the notable mishaps related to smart contract security in recent times.
- In January 2022, The Tinyman exchange based on the Algorand blockchain incurred more than $3 million in theft.
- In February 2022, almost $320 million were drained off from Ethereum and Solana in the Wormhole Cross Chain Bridge Attack.
- Most recently, thousands of Solana wallets lost around $8 million in August 2022 due to issues related to importing accounts.
- Hackers had successfully carried out a crypt heist worth $613 million in August 2021 through smart contract vulnerabilities from the Poly Network.
- The earlier examples of smart contract security problems such as theft of $150 million from Parity technologies and the $50 million theft from Genesis DAO.
Want to get an in-depth understanding of Solidity concepts? Join the Standard & Premium Plans and get free access to Solidity Fundamentals Course
Now!
Smart Contract Security Risks
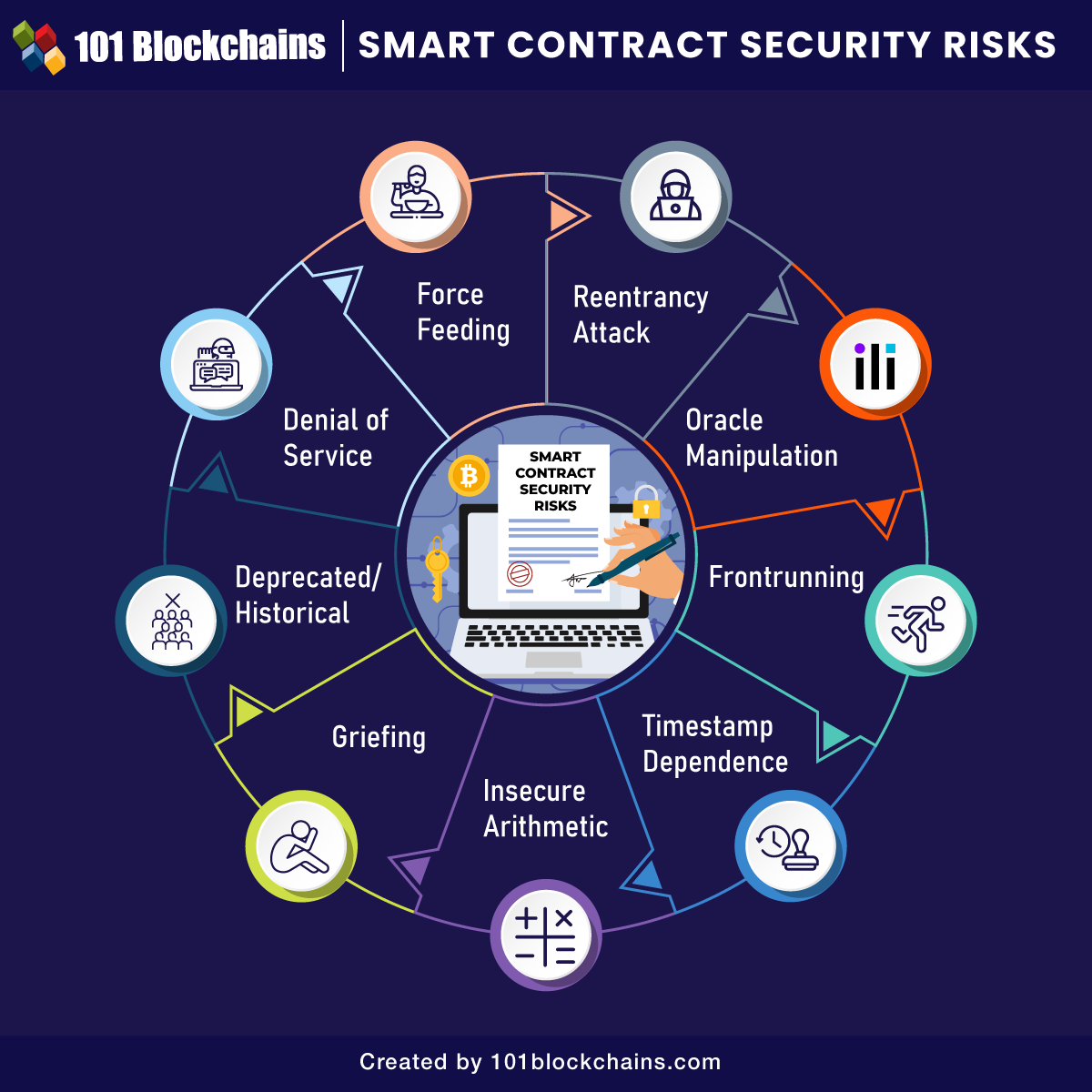
The most striking highlight in any smart contract security guide would focus on the list of known security risks. You must have a detailed awareness of the popular attacks you must worry about in the case of smart contract security. Here are some of the notable risks for smart contract security.
-
Reentrancy Attack
Reentrancy attacks are evident when exploiters can call functions repeatedly before the end of the first invocation. Malicious agents can use the reentrancy bug to withdraw balances multiple times.
-
Oracle Manipulation
The manipulation of external data providers, as well as the possible solutions for security issues with oracles, would also affect smart contract security.
-
Frontrunning
Frontrunning attacks could imply malicious use of the transaction processing approach of blockchain technology. Bad actors could add a higher fee for processing their transactions first, thereby holding off large transactions. When the large transaction reduces the token price, the malicious agents could sell the tokens they have bought.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
-
Timestamp Dependence
The outline of smart contract security best practices would also focus on timestamp dependence. It is generally responsible for attacks associated with a transaction’s timing.
-
Insecure Arithmetic
The integer overflows and underflows also present another formidable security risk for smart contracts. Ethereum Virtual Machine or EVM utilizes fixed-size data for all types of integers. When an integer variable could only support storage for numbers between 0 and 255, you would encounter overflow or underflow depending on the input value. Insecure arithmetic can also result in vulnerabilities which can help attackers in developing unprecedented logic flows.
-
Griefing
One of the notable highlights of smart contract security tools would refer to the resolution of griefing. Such types of attacks are associated with bad-faith players within a smart contract ecosystem.
-
Deprecated/Historical
Deprecated/historical attacks are associated with the history and vulnerabilities of the Ethereum blockchain. You can find solutions for such smart contract security problems on the compiler level.
-
Denial of Service
The smart contract security issues with denial of service attacks generally showcase unexpected reverts alongside a rise in block gas limits.
-
Force Feeding
Another notable smart contract security risk you must watch out for is force-feeding. It works by forcing the transfer of Ether to smart contracts for the manipulation of balance checks.
Tools for Smart Contract Security
The identification of common vulnerabilities in smart contract security offers a credible foundation for building an effective smart contract risk mitigation strategy. However, you would need smart contract security tools to detect vulnerabilities and maintain better code quality. Here are some of the notable tools which can help you reduce the possibilities and effects of smart contract vulnerabilities.
-
Visualization
Visualization tools, as the name implies, focus on visualizing smart contracts, the related control flow graphs, and EVM bytecode. The detailed visualization of what goes inside a smart contract is one of the trusted methods for safeguarding smart contracts.
-
Classification
The scope for smart contract security also involves the use of resources that can support the classification of weaknesses and vulnerabilities in smart contracts.
-
Static and Dynamic Analysis
Another set of crucial tools in any smart contract security guide would refer to static and dynamic analysis tools. The tools depend on different methods of program analysis for identifying weaknesses and vulnerabilities in smart contracts.
-
Linters and Formatters
The strategic approach for smart contract security can also make the most of linters and formatters. They help highlight the code discrepancies alongside ensuring compliance of the smart contract code to specific format standards.
-
Testing
One of the most significant highlights among tools for resolving smart contract security issues would reflect on testing. Testing tools are essential for the implementation, measurement, monitoring, and management of tests meant for smart contracts.
Start learning Smart Contracts and its development tools with World’s first Smart Contracts Skill Path with quality resources tailored by industry experts Now!
The Importance of Smart Contract Audits
Security risks for smart contracts and the tools available for ensuring smart contract security present a clear glimpse of the existing state of smart contract security. You know the issues and the tools you can use to solve the problems. However, it is important to understand that smart contracts and flexible and can adapt to changing conditions. Smart contracts hold the authority for the allocation of high-value resources among complicated systems, thereby calling for security and consistency. Interestingly, smart contract audits could help in examining the code underlying a smart contract for identifying vulnerabilities before deployment.
The need for security in the case of smart contracts becomes more profound with each passing day. In the face of many issues regarding security, inefficiency, and inappropriate behavior, smart contract security remains in the shadows of doubt. Trivial errors in smart contract code can cost an organization millions, or even billions, of dollars. Therefore, the smart contract security audit has become one of the mandatory requirements before deploying smart contracts. Here is an outline of the important reasons to choose smart contract audits as a mandatory component in smart contract security strategies.
- Early audits for the smart code could help in avoiding unwanted costs due to errors.
- Veteran security auditors can provide expert insights and reviews for the code.
- Frequent security assessments could contribute to a better development environment.
- Smart contract audits help in the proactive identification of security risks for smart contract codes.
- Frequent audits for smart contracts during the development lifecycle can help in obtaining analytical insights, such as an executive summary or details of vulnerabilities.
Announcement – Smart Contracts Security Course Launched, Explore to learn about the critical vulnerabilities and security risks in smart contract development.
Process for Smart Contract Security Audits
The discussion on smart contract security best practices would also highlight the steps in a simple, smart contract audit. Even if different auditors can include unique highlights in their approaches, the following steps are a part of the standard procedure.
-
Collection of Models for Code Design
Auditors collect details regarding code specification followed by ensuring examination of the architecture for ensuring integration of third-party smart contracts. The step is crucial for helping auditors understand the different objectives and scope of the project.
-
Use Unit Tests
The process of smart contract security audit would then turn towards running unit tests. Auditors would test each smart contract function to determine its usability. In this step, auditors would rely on manual as well as automated tools for including the overall code of the smart contract in unit test cases.
-
Choice of Auditing Method
Smart contract audits would emphasize the selection of auditing methods, as manual and automated audits have distinct advantages. In most cases, manual audits can exercise more efficiency in comparison to automated audits. Auditors do not have to rely on any software with manual smart contract audits and could also detect attacks, such as frontrunning.
-
Drafting and Publishing the Audit Report
The final step in the smart contract audit involves drafting the initial report. Once the first stage of the audit is complete, the auditors will outline the code issues and provide recommendations for resolving the errors. Upon fixing the bugs, auditors have to come up with the final report showcasing the remedial actions implemented by the project team.
Want to understand the importance of smart contracts audits? Check here Smart Contract Audit – A Detailed Guide Presentation now!
Best Practices for Smart Contract Security
The collection of smart contract security tools and the benefits of audits could only get you to an extent in securing smart contracts. Smart contract security is not an objective. On the contrary, it is a methodology, and you need to prepare for the dynamic changes in the smart contract landscape. The applications of smart contracts are changing, and so are the principles behind their working and security. Here are some of the best practices for smart contract security.
- Always prepare for failure and strive to make your code as resilient as possible with every attempt.
- One of the trusted practices to deal with smart contract security issues refers to maintaining track of new developments in security.
- Another simple practice to avoid smart contract security risks would point to avoiding complexity in the smart contract logic and code.
Excited to know about top smart contract development tools to help you build smart contracts? Check the detailed guide Now on 10 Best Tools For Smart Contract Development
Final Words
The final impression regarding smart contract security suggests that developers have to improve their contracts to deal with new problems. A detailed overview of smart contract security risks is an obvious starting point for identifying the seriousness of the situation. In addition, the smart contract security guide also highlighted examples of popular smart contract security mishaps. As smart contracts become the mandatory ingredient for driving revolution in the future of web3, it is important to worry about their security. Interestingly, you can use reliable tools and follow a few simple best practices for safeguarding smart contracts. Learn more about smart contract security and become a certified blockchain security expert now.