Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Decentralized Finance
Diego Geroni
- on November 26, 2021
Understanding Security Risks in DeFi
Wondering if there is any security loophole in Decentralized Finance (DeFi)? The answer is yes, and in this discussion, we’ll learn about the different security risks in DeFi. Let’s dive in!
Decentralized finance or DeFi provides a clear description for an emerging ecosystem of blockchain-based alternative financial systems. DeFi platforms help users in engaging in different traditional financial transactions such as lending and borrowing through direct P2P exchanges. As a result, they can remove the need for traditional financial intermediaries and offer direct reconciliation for the transfer of value.
However, the growing popularity of DeFi has also drawn attention towards DeFi security risks for many obvious reasons. The following discussion helps you discover a comprehensive outline of some of the prominent security risks in DeFi with an explanation. A detailed overview of the security risks associated with DeFi can help you discover the best practices for using DeFi.
Want to explore an in-depth understanding of security threats in DeFi projects? Enroll In DeFi Security Fundamentals Course Now!
Understand the Vulnerability of DeFi Ecosystem
DeFi or decentralized finance, as the name implies, provides decentralized access to financial services. DeFi leverages open protocols and decentralized applications empowered by smart contracts. You can get a better understanding of DeFi risks by identifying the core elements in their functionality.
Smart contracts are indeed a crucial aspect of DeFi as they replace the role of conventional centralized financial institutions. However, smart contracts are just code, and any compromises in the code could lead to loss of funds. On the other hand, hackers are always seeking opportunities for breaching the DeFi ecosystem through any of the dApps or users in the ecosystem.
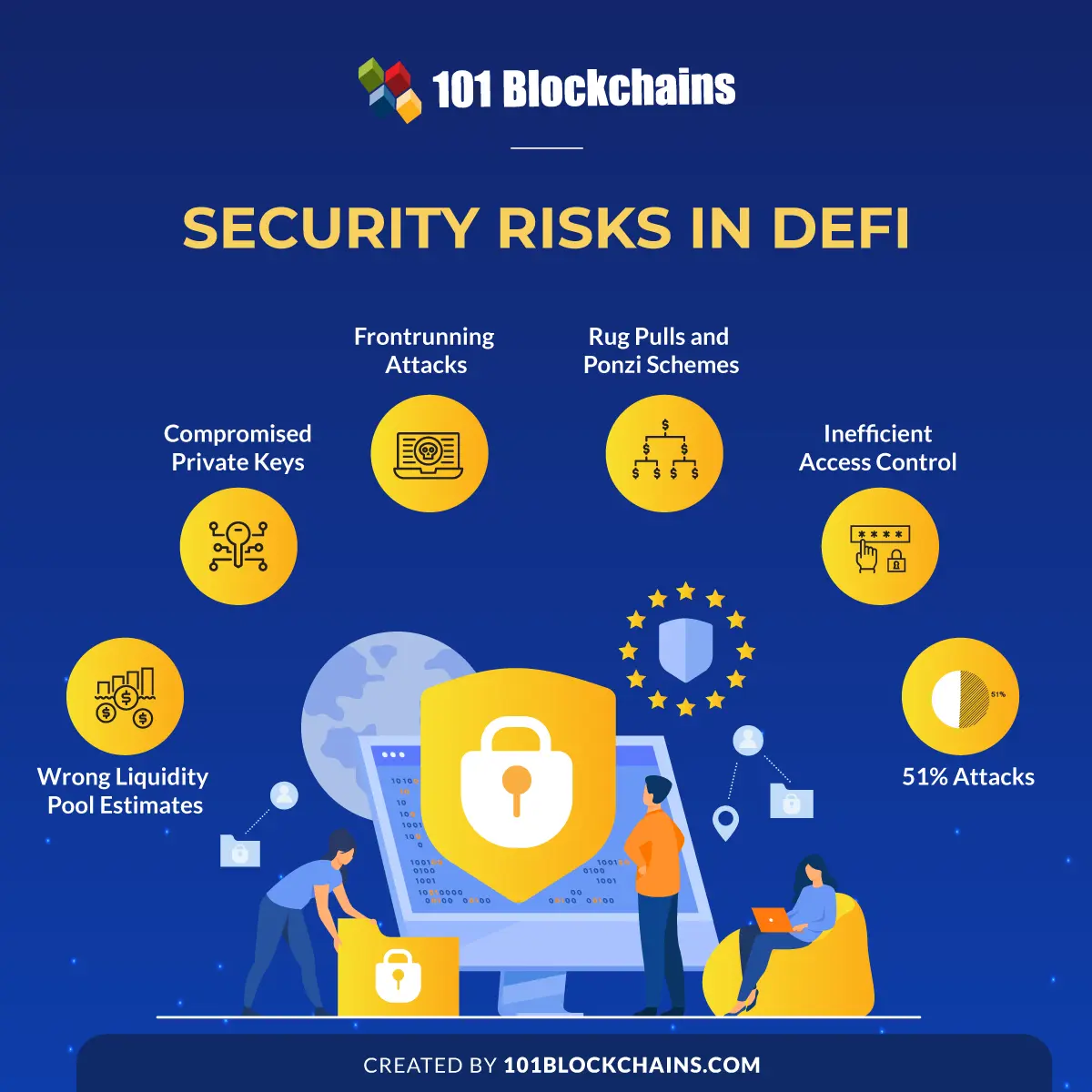
What are the Security Risks in DeFi?
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2021/11/Security-Risks-in-DeFi-1.png' alt='Security Risks in DeFi='0' /> </a>
As of mid-2020, DeFi has been experiencing profound levels of growth. The total value locked in DeFi protocols in August 2021 was almost $75 billion. With such massive amounts of money placed at stake throughout different DeFi protocols, it is important to identify decentralized finance security risks. The identification of security risks in the domain of DeFi could help in anticipating productive safeguards for the massive investments in DeFi protocols. Here are some of the notable entries among DeFi security risks you should be careful of.
Want to know what is the scope and purpose of DeFi? Enroll Now: Introduction to DeFi – Decentralized Finance Course
-
Wrong Liquidity Pool Estimates
The most general issue leading to security risks in DeFi is the incorrect calculation of the value of tokens in the liquidity pool. DeFi users invest their tokens in a liquidity pool and receive a stake which helps them in obtaining value in the future. Generally, the liquidity pools evaluate the value of tokens in the pool according to the existing composition of the pool rather than depending on external oracles.
Attackers could capitalize on this discrepancy in one of the common DeFi attacks, such as flash loan attacks. Attackers could introduce radical imbalances in the pool for the duration of a specific transaction. The unbalanced pool could result in incorrect calculation of token value while enabling attackers to compromise value in the pool.
Want to understand the best ways to use DeFi development tools like Solidity, React, and Hardhat? Enroll now in DeFi Development Course!
-
Compromised Private Keys
Another formidable issue that emerges among security risks in DeFi would refer to stolen or leaked private keys. Blockchain protocols leverage cryptography for managing access and control of blockchain accounts. Private keys are basically the PIN code you need to access transactions sent to your public key address. Therefore, many of the prominent DeFi risks emerge from the possibilities of compromised private keys. Interestingly, there are various possible ways for leaking or theft of private keys.
The first entry among the types of attacks on private keys includes a compromised MetaMask interface. MetaMask is a popular application tailored for interacting with the Ethereum blockchain and performing transactions on it. Different DeFi projects, as well as users, have experienced losses of crypto by using malicious versions of MetaMask.
The DeFi security risks due to stolen and leaked private keys also emerge due to poor practices for key generation. It is important to use a secure random number generator for generating private keys. However, generating the keys by using a poor source of randomness could make the private keys vulnerable to hackers. How? Poor private keys are easy to guess, and hackers could easily gain control over the user’s blockchain account.
Another potential way in which you can lose private keys leading to common DeFi attacks refers to loss or theft of the seed phrase. The seed phrase or mnemonic phrases offer an easier way of remembering private keys. However, many notable DeFi hacks in recent times involved the accidental exposure or theft of the seed phrase.
Want to explore in-depth about DeFi protocol and its use cases? Enroll in Decentralized Finance (Defi) Course- Intermediate Level Now!
-
Frontrunning Attacks
The next important addition among DeFi security risks would point towards front-running attacks. You should note that blockchains do not add transactions immediately to the distributed ledger. On the other hand, transactions have to be broadcasted throughout the blockchain network upon creation. Subsequently, the transactions are stored in mempools of each blockchain node prior to their addition to the ledger in blocks.
The time between creating a transaction and including it in the ledger is a gleaming opportunity for front-running attacks. Attackers would generally seek out the transactions which they could compromise by leveraging the Miner Extractable Value. In event of identification of opportunity for frontrunning attacks, the attackers would create their own variant of the transaction with higher transaction fees before transmitting it to the network. Blockchain miners generally arrange the transactions in the order of their transaction fees. So, with the attacker’s transaction coming prior to the original one, they could easily grab profits. Frontrunning security risks in DeFi could have varying levels of impact.
First of all, many attackers or bots would leverage frontrunning for making profits according to their prior knowledge of transactions of a user. However, in some cases, the attackers would stage an attempted exploit followed by returning the compromised tokens to the exploited protocol.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
-
Rug Pulls and Ponzi Schemes
Another top entry among decentralized finance security risks would obviously refer to rug pulls and Ponzi schemes. Various DeFi protocol attacks emerge from external threats, albeit not in all cases. Alarmingly, DeFi users can also be victims of attacks by the owners and developers of the protocol.
Rug pulls are one of the most common examples of insider attacks in DeFi. It is one of the common DeFi attacks in which an individual in the company having access to the company’s contracts misuses their privileges for draining value from the protocol. In all cases, the project and the team disappear into oblivion with little left to solve the issue.
-
Inefficient Access Control
The majority of DeFi smart contracts leverage the use of privileged functions, which is also responsible for one of the common DeFi security risks. The privileged functions are specially tailored so that the owner of the smart contracts can call the functions. In addition, the contract owner also has access controls for enforcing the functions. The most common approach for managing access is through the specification of calls to the function, which should be performed by one or multiple addresses from a collection of addresses.
Alarmingly, the access controls are implemented wrongly or not at all, thereby opening up doors for attackers. Hackers could gain privileged access to a smart contract, and they could exploit value by using the smart contract to their advantage.
-
51% Attacks
The final entry among the different types of decentralized finance security risks would obviously point towards 51% attacks. You should note that the 51% attack is one of the most common threats in blockchain security. 51% attack is more common in the case of Proof-of-Work protocols and arises primarily due to the design of blockchain consensus algorithms. It is clearly evident that blockchain consensus algorithms leverage some type of majority vote, and in Proof-of-Work, miners use their computational power for voting.
In the case of 51% attacks, attackers gain control over a major share of the computational power of a blockchain. As a result, they could easily ensure faster growth of their blockchain in comparison to legitimate blockchains. Subsequently, attackers could exploit the security risks in DeFi through the 51% attack and rewrite the contents of the distributed ledger. Most importantly, 51% attacks could also open up possibilities for double-spend attacks. Therefore, 51% attacks could easily threaten the security of DeFi protocols running on smart contracts.
Best Practices for DeFi Security
While there are so many notable DeFi risks, you can turn towards some best practices to ensure safety from them. One of the common recommendations in best practices for DeFi security refers to smart contract audits. In addition, the use of DeFi-related monitoring and ranking tools can help in reviewing security information regarding DeFi protocols. Furthermore, risk management solutions and monitoring network health could also serve as vital practices in resolving DeFi security risks.
Excited to learn about the critical vulnerabilities and security risks in smart contract development, Enroll now in the Smart Contracts Security Course!
Bottom Line
The most important highlight about DeFi points out the complexity of its work. Everything is out in the open with smart contracts, and DeFi aims to open financial services more to the general public. So, it is reasonable to expect security risks in DeFi, which could affect users. The wide variety of decentralized applications emerging in the DeFi ecosystem presents new opportunities for attackers to exploit DeFi vulnerabilities.
Some of the notable security risks include frontrunning attacks, 51% attacks, rug pulls, and discrepancies in access control. With a clear impression of different security risks associated with DeFi, users could identify productive ways for using DeFi solutions. Learn more about DeFi and explore the best practices for addressing security risks in the domain.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!



![30+ Best Decentralized Finance Applications [Updated] best decentralized finance (DeFi) applications](https://101blockchains.com/wp-content/uploads/2020/10/decentralized-finance-applications.png)