Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!
- Guides
Diego Geroni
- on June 10, 2021
An Introduction to zkSNARKs
Privacy is one of the most crucial features that you can find in the blockchain landscape. Blockchain has been the founding platform for many new concepts such as zkSNARKs which are the cryptographic techniques for ensuring privacy in the blockchain. Privacy is an important requirement when it comes to the crypto landscape, especially with the applications in Zcash, a blockchain-based payment system driven by JP Morgan Chase.
Zcash also provides an approach for secure authentication of clients to servers and is a popular zk-snarks example. At the same time, the application of zk-snarks on Ethereum is also one of the topics of attention in the blockchain and crypto landscape. So, what is zk-snark, and why is it important now? The following discussion dives into important details about zk-snarks and their implementation.
Excited to understand the core concepts of zero-knowledge proofs, Enroll Now in Zero Knowledge Proofs (ZKP) Masterclass
Understanding Zero-Knowledge Proofs
Zero-Knowledge Proofs (ZKPs) emerged with the sole intention of offering a safer approach for conducting information exchange and other transactions. As a matter of fact, any account of zk snarks explained clearly would feature an impression of zero-knowledge proofs. Cryptographer Jean-Jacques Quisquater and his collaborators published a paper with the title ‘How to Explain Zero-Knowledge Protocols to Your Children’.
The paper provided an introduction to zero-knowledge proofs. It featured a simple example of Ali Baba’s Cave, which has been used several times. Many variations of Ali Baba’s Cave example have been used for explaining ZKPs, especially zkSNARKs. However, the basic information underlying the example is practically the same in every variation.
The Ali Baba Cave Example
The Ali Baba’s Cave example involves a ring-shaped cave that has a single entry and a magical doorway setting the two side paths different from each other. If you have to pass through the magic doorway, then you have to whisper the correct secret words. Now, Jenny wants to prove to John that she knows the secret words without disclosing them to John. In order to achieve the same, John decides to wait outside, and Jenny steps inside the cave before reaching the end of one of the two paths. Now, Jenny decides to enter the cave through the first path, and John comes to the entrance of the cave.
The condition, in this case, is that John wants Jenny to come out of the cave in another path. If Jenny knows the secret words, she can open the magic doorway and come through the path requested by John. Now, John could repeat the process many times to ensure that Jenny is not guessing the secret words.
Therefore, Ali Baba’s Cave example clearly showcases zero-knowledge proofs. Above all, ZKPs are the foundation of zksnarks Ethereum implementations and their other applications. ZKPs help in proving ownership of specific knowledge without disclosing any information about the same.
Excited to learn the basic and advanced concepts of ethereum technology? Enroll Now in The Complete Ethereum Technology Course
What are ZKSNARKS?
It is important to learn about the definition of zk-snarks in any introductory article on them. One of the first questions that you may have is ‘what does ZK-snark stand for?’ and the answer is simple.
The ‘zk’ in zk-snark stands for ‘zero-knowledge.’ On the other hand, ‘snark’ means Succinct Non-Interactive Argument of Knowledge. Combine both of them, and you get ‘Zero-Knowledge Succinct Non-Interactive Argument of Knowledge’ i.s. ZK-SNARKS.
The foremost example of a zk-snarks coin points out to Zcash, which is their first widespread application. Interestingly, zk-snarks is a new form of zero-knowledge cryptography. Zcash is a cryptocurrency with the assurance of privacy for all users. The privacy assurance offered by Zcash largely relies on the flexibility for full encryption of all shielded transactions on Zcash. At the same time, the shielded transactions are easily verifiable according to the consensus rules in the network with zkSNARKs. Zcash is definitely a good example of zk-snarks and offers an adequate opportunity to understand them well.
Want to learn about consensus algorithms? Read here for a detailed guide on Consensus Algorithms: The Root Of Blockchain Technology now!
Components and Characteristics of ZKSNARKS
As mentioned above, the term zk-snarks stands for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge. Let us break down each component that makes up zk-snarks for understanding them well.
-
Zero-Knowledge
The first aspect in zk-snarks is ‘zero-knowledge’. As mentioned already, zero-knowledge proofs help one party to prove the truth of a statement to another party. Note that, the former party in a zero-knowledge proof is known as the prover, and the latter is known as the verifier. The prover can prove the truth of a statement to the verifier with ZKPs without revealing any other information. For example, zero-knowledge proofs are helpful in cases where the verifier can give the hash of a random number to the prover. However, the prover could convince the verifier that the hash value is related to a specific number without revealing the number itself.
-
Succinctness
The next important component in zk-snark blockchain refers to succinctness. The ‘succinct’ trait in zk-snarks implies that the size of the messages is very trivial in comparison to the transaction. Therefore, succinct ZKPs are easily verifiable within a matter of milliseconds. Proof length generally ranges up to some hundred bytes, even for statements regarding massive programs.
Curious about ZKPs’ Examples? Read here for an Example Of A Good Zero Knowledge Proof now!
-
Non-Interactive
The characteristics of zk-snarks also refer to the non-interactive zero-knowledge proof. As the name implies, non-interactive ZKPs could ensure that there is complete none or very limited prover-verifier interaction. In the case of zk-snarks, you can find only a setup phase. Following the setup phase, a single message goes from the prover to the verifier. Interestingly, zk-snarks also features the ‘public verifier’ property which helps in enabling any individual to verify without new interactions.
-
Argument
The understanding of zk-snark blockchain applications also depends a lot on arguments. Arguments basically imply protection for the verifier against the prover with computational limitations. Any prover with adequate computational power could create arguments or proofs regarding wrong statements. Interestingly, the right amount of computational power could help in breaking down public-key encryption. The use of arguments could help in ensuring computational soundness with zk-snarks.
-
Knowledge
Knowledge is the final element in zkSNARKs and is quite crucial for the efficiency of the cryptograpy technique. Any prover could not create a proof or argument without knowledge of any particular witness. The witness could be the path to a specific Merkle-tree node, address where provers want to spend from, and the preimage of a hash function.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
Creating ZK-SNARKs
The most efficient approach for creating a zk-snarks example is the initial setup phase. The initial setup phase is important for creating a common reference string that could be shared between verifier and prover. The common reference string is helpful for creating non-interactive and short ZKPs which are eligible for publication on the blockchain. You can find this system on Zcash, which considers the common reference string as the system’s public parameters.
Zcash employs an elaborate ceremony involving multiple parties for generating public parameters. The Parameter Generation Ceremony is important for preventing access to the randomness involved in generating the parameters. Without the Parameter Generation Ceremony, anyone could generate false proofs that would apparently appear valid to the verifier. In the case of Zcash zkSNARKs example, the Parameter Generation Ceremony ensures that malicious parties couldn’t create counterfeit coins.
Practical Examples of ZK-SNARKS in Zcash
The approach for creating zk-snarks coins such as Zcash can help in widening your knowledge of them. As Zcash primarily focuses on zero-knowledge privacy. Imagine a function that has to find the validity of a transaction according to the consensus rules of the network. The function must return the answer about the validity of the transaction without exposing the underlying information. Encoding the network’s consensus rules in zkSNARKs can help in achieving the same. On a high level, zk-snarks start working by a series of transformations. First of all, they transform what you want to prove into proof of knowledge regarding a solution to certain algebraic equations.
So, let us find out the ways of transformation of rules for valid transactions in equations which you can evaluate for a candidate solution. Remember that, you would still not reveal sensitive information to the parties involved in equation verification.
-
Create an Arithmetic Circuit
The foremost step in the transformation of function for transaction validity into mathematical representation involves breaking down logical steps. The breakdown of logical steps into the smallest possible operations can create a suitable ‘arithmetic circuit.’ The arithmetic circuit is an important requirement in zkSNARKs implementation and is similar to a Boolean circuit. The arithmetic circuit involves breaking down a program into individual steps having fundamental arithmetic operations.
One of the fundamental examples of an arithmetic circuit appearance for computing the expression like (a + b)*(b*c) is as follows,
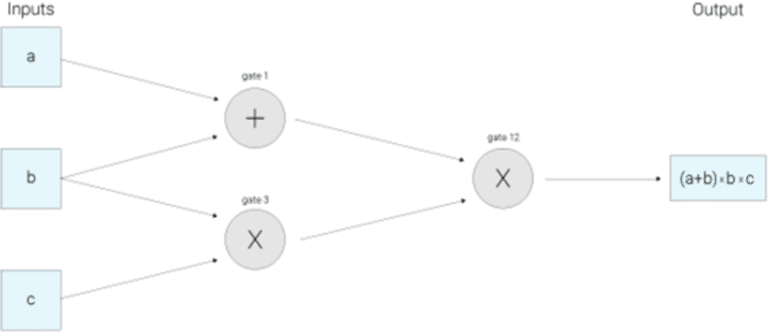
Image Source: https://z.cash/technology/zksnarks/
The circuit outlined in zk-snarks explained accounts suggests that input values a, b and c, are just moving from left to right on the wires towards the output gate.
-
Create R1CS Mechanism
The second step in zk-snarks example creation refers to the creation of a Rank 1 Constraint System or R1CS. The R1CS is important for checking whether the values are moving correctly in the right direction. In the concerned example, the R1CS can confirm that the value coming from the multiplication gate with ‘b’ and ‘c’ as the inputs would be b*c. The R1CS representation provided here implies that the verifier must check various constraints, with one for every circuit wire.
Interestingly, a 2012 paper on the R1CS mechanism showcased a favorable approach for bundling all constraints into one. The paper presented a method for non-interactive zero-knowledge proof creation with Quadratic Arithmetic Program (QAP) as a representation of the circuit. The single constraint in this case that is eligible for assessment can be found between polynomials and not numbers.
Users should note that the polynomials can be large. However, it provides promising advantages. An identity that fails to hold well between polynomials can also fail in verification at other points. So, users have to verify that two polynomials align perfectly at a randomly selected point. This helps in the correct verification of the proof with assurance of high probability.
-
Use of Elliptic Curves
The application of elliptic curves is also one of the important aspects of understanding about zkSNARKs. A prover with knowledge about the point that a verifier would select for assessment could create invalid polynomials. The alarming factor here is that the invalid polynomials could satisfy identity at a particular point.
In the case of zk-snarks, advanced mathematical techniques like elliptic curve pairing and homomorphic encryption could help in blind evaluation. Blind evaluation of polynomials basically means that you don’t know the point under evaluation. The public parameters can help in determining the point to be checked. However, elliptic curve pairing ensures that both the prover and verifier are unaware of the point of identity assessment.
Finally, users should also understand how to add zero-knowledge or ‘zk’ in zk-snark blockchain applications. The elements covered in the design of zk-snarks till now show how you can get a short, non-interactive, and single message proof. The ‘zk’ part is important for ensuring the confidentiality of secret inputs. Interestingly, it is easy to add ‘zk’ part if the prover uses ‘random shifts’ of the original polynomials. Most important of all, the polynomials should have the capability to satisfy the required identity.
Wondering about the role of Zero Knowledge Proofs in Blockchain? Check here How Zero Knowledge Proofs are Changing Blockchain
Future Applications of ZKSNARKs
The foremost example of zk-snarks Ethereum or other blockchain applications is evident in identification or authentication approaches. ZKSNARKs are crucial for safeguarding user privacy when they prove identity in the authentication process. Blockchain applications relying on identification or authentication could leverage zk-snark mechanisms for allowing access. They cannot reveal information regarding the user. Therefore, zk-snarks can help in achieving a trustless environment like a public blockchain. ZK-SNARKs could help verifiers in storing the proof calculated by the Prover like a transaction on a blockchain.
As the zk-snarks implementation in Zcash clearly shows, they are also suitable for applications in the financial world also. The primary focus of zk-snarks on the Ethereum network alongside Zcash indicates its ambitious plans. Zk-snarks can ensure faster financial transactions in shorter time durations.
Final Words
On a final note, the detailed overview of zkSNARKs suggests that they could be the next big thing for blockchain. Tailored for cryptocurrency transaction efficiency, zk-snarks can unravel new possibilities for strengthening privacy. At the same time, zk-snarks don’t compromise on the speed of transactions or accessibility.
Most important of all, the individual traits of zk-snarks make them ideal for blockchain applications that require privacy. The creation of zk-snarks also presents insightful ideas regarding their effectiveness and functionality. Start exploring more about the future projects based on zk-snarks to understand their potential. You can learn about zk-snarks as just another cryptographic technique or advancement in the overall blockchain ecosystem.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!