Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!

- Blockchain
101 Blockchains
- on March 29, 2019
Know Everything About Blockchain Proof Of Work (PoW)
The blockchain craze is slowly turning into an opportunity to overhaul legacy systems and make them more productive. However, there is much more that people need to know about blockchain to appreciate the ingenuity that lies at its core. One of the core aspects of the technology is blockchain proof of work algorithm.
Blockchain technology is still in its infancy, so to speak, but there is already huge potential in terms of what it can help to achieve. Notably, the technology is transitioning from the basic framework on which cryptocurrencies run to something of a technology that is revolutionizing industries.
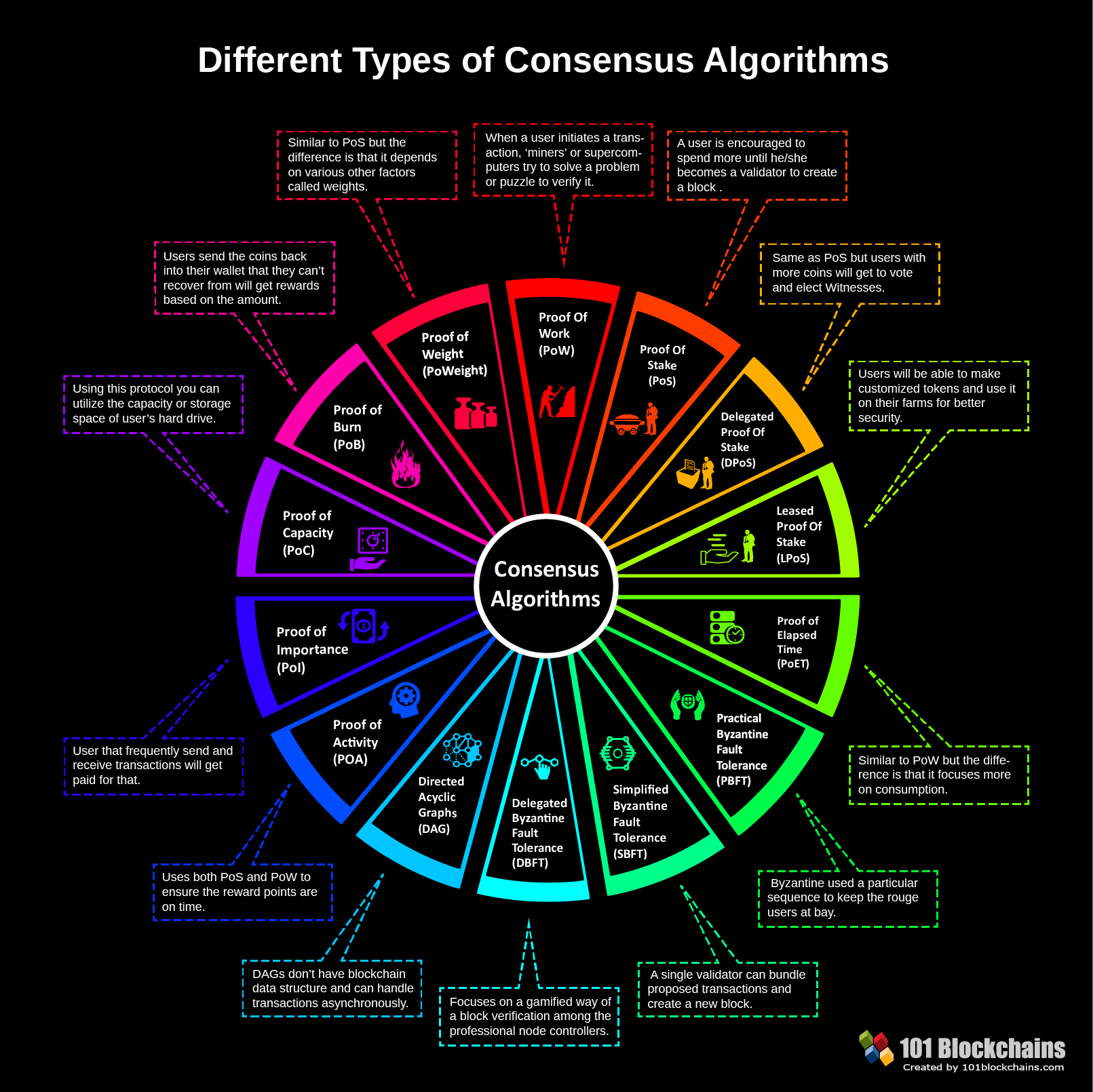
What is a consensus algorithm?
Basically, the technology allows users to interact on a peer-to-peer basis and without a central authority. Notably, transactions are completed when there is consensus throughout the network. In particular, the consensus algorithm is what sets different blockchain networks apart. For instance, the Bitcoin network differs from the Ethereum network based on the consensus algorithm.
Technically, a consensus algorithm is the process of decision making within a group. Notably, the members of the group come up with a system that streamlines the process through which they can find common ground regarding a certain subject. For consensus to happen, at least the majority of the participants within a group should agree and the decision at hand must be able to benefit that majority.
Interestingly, blockchain consensus algorithms operate using a similar logic. In addition to that, the blockchain consensus algorithms have specific objectives that seek to boost usage of the blockchain networks. Firstly, the algorithm undertakes to collect as much agreement among the participating nodes as possible such that there is widespread agreement.
Secondly, the widespread agreement within the network is supposed to facilitate collaboration among the participants. In particular, the algorithm ensures that whatever agreement that the participants agree on serves the interests of all the members. Third, the agreement fosters cooperation such that every individual works toward the collective interest of the network.
Further, the algorithm strives to make sure that all participants have equal rights as a peer-to-peer relationship should be. Ultimately, the fostering of an environment where everyone has equal rights facilitates participation and individual activity of the participants.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
Types of consensus algorithms
Like earlier explained, there are different types of consensus algorithms and on the basis of which different blockchain networks exist. Notably, every algorithm has its own unique characteristics that distinguish it and that achieve consensus within the network via different mechanisms. Currently, there are quite a number of blockchain consensus algorithms. However, the two major ones are Proof-of-Work (PoW) and Proof-of-Stake (PoS).
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2018/08/Different_Consensus_Algorithms.png' alt='Consensus Algorithms Infographic='0' /> </a>
What is the Blockchain Proof-of-Work Algorithm?
This is the oldest consensus mechanism and one that is the most popular currently. Notably, the first mention of the algorithms pre-dates the invention of the Bitcoin network. Interestingly, research into the algorithm goes back to the early ‘90s where Moni Naor and Cynthia Dwork published an article in 1993. In the article, the authors explored the potential of the algorithm to prevent fraud.
In 1999, another researcher in cryptography, Markus Jakobsson coined the term “Proof-of-Work” and it stuck until when Satoshi Nakamoto surprised the world with the invention of bitcoin. In particular, the Bitcoin blockchain network is simply an implementation of the research whose first steps date back to 1993.
The PoW algorithm remains the most popular because it among the few that cannot be compromised. In technical terms, it is one among those algorithms that can attain the Byzantine Fault Tolerance. Notably, the Byzantine Fault Tolerance (BFT) is simply the capability of a system to withstand failures that are associated with the Byzantine Generals’ Problem.
This is to say that the network can successfully avoid situations where some nodes can attempt to act against the consensus. In the context of blockchain technology, it is obvious that blockchain networks do not have a central authority to moderate transactions. Instead, the public ledger is distributed among all the participants hence blockchain technology also known as a distributed ledger technology (DLT).
Given the valuable information stored on the public ledgers, there is a high probability that some bad actors might want to cause faults for selfish gains. As such, these bad actors present the Byzantine Generals’ Problem. This way, there is need for the blockchain network to have the Byzantine Fault Tolerance to avoid such problems.
Curious to learn about blockchain implementation and strategies? Enroll Now in Blockchain Technology – Implementation And Strategy Course!
How does the PoW work?
Clearly, the PoW algorithm is very secure since it can withstand the BFT. Interestingly, it is the manner in which it operates that makes it even more secure, hence quite popular. Without the BFT characteristic, a member of a network can falsify transactions and hence compromise the reliability of the block generated by the transaction.
A PoW algorithm works in such a way that nodes within a network need to solve a mathematical problem so that they can create the next block. Whoever is the first one to get the solution to the mathematical problem gets the consensus permission to choose the block that should be added next to the platform.
As a result, this successful node gets currency as a reward. In a bitcoin network, the reward a bitcoin token. Therefore, there is the incentive to continue solving the mathematical problems so that one can get the permission to choose the next block. Also, it is clear now why some nodes would like to falsify transactions and hence the need for Byzantine Fault Tolerance.
Nevertheless, it is not easy to get the answer to the mathematical problem. In that case, nodes have to find the solution to the problem via brute force. This is to say that those nodes that have the highest computational power are the most likely to find the solution to the mathematical problem. Notably, these nodes that participate in the computation are called miners and the process of solving the problem is called mining.
Please include attribution to 101blockchains.com with this graphic. <a href='https://101blockchains.com/blockchain-infographics/'> <img src='https://101blockchains.com/wp-content/uploads/2018/08/PoW.png' alt='blockchain proof of work algorithm='0' /> </a>
Why Blockchain Proof of Work is successful
The process of mining is energy intensive since it requires greater computational capability to solve each successive problem. As such, the process consumes a lot of electrical power. We shall look at this aspect later and why it is one of the reasons people are moving away from the algorithm to other alternatives. Nevertheless, PoW is quite successful at the moment for two reasons.
Firstly, getting the solution to the mathematical problem is quite hard. Therefore, nodes need to spend time in computations which are cumbersome. Interestingly, the supply for computational power is quite tight and this is to say that few actors have access it. Interestingly, this characteristic is also the reason behind the impossibility of nodes cheating during transactions.
For instance, let us assume that a bad actor wants to attack the network and fault data registered on a certain block. If the whole network has ten blocks and the target block for the bad actor is number seven, the bad actor will need to alter that data for block ten, nine eight and then seven, which is the target. Given the computational power required to mine a single block, it is close to impossible for one to alter data on four blocks. Basically, there is no computer with the capability to solve such a problem.
Secondly, PoW is successful because, once a node creates a block, other nodes can easily verify the process that led to the solution. Notably, this is partly due to the nature of the problem in need of a solution. To solve the problem, the miner has to arrive at an answer that is less than a preset value.
For instance, the network can put forward a value like 10. In order for the solution to be correct, one will have to make sure that the solution is less than 10 i.e. nine. If a miner successfully arrives at nine, the other nodes will easily follow the procedure with which the miner used to get to the solution. However, it gets complicated if the transaction is falsified.
A comparison of the proof of work and the proof of stake algorithms
| Characteristic | Blockchain Proof of work | Blockchain Proof of stake |
|---|---|---|
| Mining | The miner is chosen through the ability to solve a complex computational problem | Anyone with a stake has the chance to be the miner and does not involve any computations |
| Validation | It takes longer because validators have to retrace the computations made by the miner | Takes shorter since there are not computations involved |
| Scalability | Since all nodes must take part in validation, the algorithm is difficult to scale | Not all nodes take part in validation and hence it is fast and highly scalable |
| Energy consumption | Quite energy intensive due to the computational nature of validation. | It is very energy efficient as it does not require any kind of computations |
| Cryptojacking | Bad actors likely to “cryptojack” other computers to provide more computational power for mining | No one is at risk of Cryptojacking since mining does not need enormous amounts of computational power |
What the future hold for proof of work?
Like earlier mentioned, proof-of-work gobbles up tons of energy to complete the computations. Interestingly, this is one of the major failing points that detractors of the algorithm call out. By November last year, reports indicated that it was twice as expensive to mine one dollar’s worth of bitcoin as gold, copper or platinum in terms of the energy spent.
According to researchers, mining one dollar’s worth of bitcoin requires over 17 megajoules of energy. Interestingly, it only takes about five megajoules to mine gold, four to mine copper and seven to mine platinum. Therefore, the venture is turning out to be much more expensive and considering that the price of the cryptocurrency is quite volatile.
Also, as more blocks add to the existing blockchain the process of solving problems for the next blocks gets harder. Notably, the computational process is much more difficult and, as such, there is need for more complex hardware that can handle the computations. As a result, the price of mining hardware is rising exponentially.
What all these issues present is a future that is somewhat bleak for this algorithm. Interestingly, there are governments that already imposed moratoriums on mining activity so that they can come up with proper legislation to cater for the high energy consumption of mining. Already, some blockchain networks like Ethereum which initially relied on PoW algorithm are migrating to other alternatives like proof-of-stake. Basically, there is a real chance that the protocol will undergo fundamental changes in an effort to rationalize its use or people will abandon it completely.
Start your blockchain journey Now with the Enterprise Blockchains Fundamentals – Free Course!
Challenges to PoW
Like earlier discussed, PoW is facing existential threats from the major challenges. In terms of energy consumption, it is already clear that the algorithm is very unforgiving when it comes to use of electricity. Add to this the rising cost of mining hardware and all one remains with a biting headache on how to handle the algorithm.
Therefore, it is clear that the major challenge the PoW algorithm is facing is the rising cost of solving the computational problems. Notably, one needs to spend an average of $4,758 in the United States to mine just one bitcoin. In Germany, the cost jumps to $14,275 while South Korea comes out as the most expensive at $26,170. Interestingly, CoinMarketCap indicates that the price of one bitcoin is currently at $4,089. Therefore, it is clear that a miner in the US, Germany and South Korea will actually accrue huge losses if the carry out any mining activity.
Another challenge that PoW algorithm is facing is that it is not truly decentralized. Knowledgeable observers point out that at any one point in time, only one node is responsible for maintaining the ledger. This is the same person who has the permission to choose what the next block will be and is the same person that will receive the reward after addition of the block.
In remedy, users of the blockchain technology are demanding for a fundamental shift in the handling of the ledgers within a blockchain network. In particular, the users want the ledgers to reside in many peers simultaneously so that to avoid the “dictator” tendency of the single node hosting the ledger at any given point. Essentially, this implies fragmenting the ledger into many pieces such that no single node has a clear picture of the contents of the ledger.
Start learning Blockchain with World’s first Blockchain Skill Paths with quality resources tailored by industry experts Now!
Blockchain proof of work algorithm alternative
In an effort to improve the blockchain space, some developers came up with alternatives to blockchain proof of work algorithm which are simply other types of consensus algorithms. So far, there are numerous alternatives, some of which were mentioned earlier. Here, we will look into only one of the alternatives which is proof of stake.
Blockchain proof of stake
As a consensus algorithm, proof of stake first came onto the blockchain scene in 2011, two years after proof of work. The major difference between proof of work and proof of stake is that users of the latter do not have to solve complex problems to achieve consensus. On the contrary, users only need to use cryptocurrency as the stake with which to achieve consensus.
Here is how it works. All the participants within a blockchain network that uses the PoS protocol must have the base cryptocurrency to participate in consensus making. For instance, if Ethereum blockchain network successfully transitions to PoS, users will need to have Ether in their accounts to participate.
For the participants that would wish to mine the next block, one will need to stake the currency that they have. Interestingly, the chances of one choosing the next block depend on the amount of crypto staked. For instance, if one’s total stake amounts to 2% of all the crypto staked in the network, the node will have a 2% chance of miming the next block.
Therefore, while mining is still present in this protocol, it is clear that it does not depend on computations like proof of work. Further, the proof of stake protocol chooses the miner randomly and he/she receives the reward in terms of the transaction fee. Therefore, there is a high probability that anyone among the validators with stakes can claim the mining responsibility. Further, there is much more decentralization since every action is randomized.
Want to become a Cryptocurrency expert? Enroll Now in Cryptocurrency Fundamentals Course
Merits of proof stake
In this case, it is obvious that the power consumption rate is almost insubstantial compared to blockchain proof of work algorithm. Going forward, protocols whose energy demand is low will assume prominence since electricity costs are on the rise. Further, the fact the algorithm consumes less energy implies that it does not require sophisticated hardware to facilitate the mining process. Ultimately, this is evidence that the protocol is cost effective both in the short-term and the long-term.
Another merit of proof of stake is the randomization of the process of selecting the node responsible for the mining process. It would have been a major setback if selection depended only on the amount of stake one has. This way, only the richest nodes in the platform would have the leeway to carry out the transactions and that they would continue growing richer.
On the contrary, the randomized process ensures that anyone with a stake has a real chance of participating in the mining process. Also, this is evidence that there is real decentralization where, unlike PoW, there is no one node in charge of the whole ledger at any point in time.
Further, the process that goes into proof or work is not only energy intensive but also time consuming. Notably, it takes between 40 and 60 minutes for validators to approve transactions in a blockchain network under the proof of work protocol. On the contrary, the process of validation in the PoS platform is quick since mining is fast and efficient. For this reason, Ethereum network expects to significantly increase the number of transactions per second once they migrate to PoS.
Want to learn the basic and advanced concepts of Ethereum? Enroll Now – Ethereum Development Fundamentals
Demerits of PoS
Unsurprisingly for a new technology that is still under development, PoS has various pitfalls that might bring trouble if encountered. First, the fact that validators only need to stake their cryptocurrency to be able to mine is a huge problem. In particular, this implies that any bad actor who can procure a very large amount of tokens can suddenly overpower all the other validators and take control of the network.
However, the laws of economics protect the network against such an attack. In particular, any sudden spike in the rate of buying tokens will trigger a sharp rise in the price of the tokens to the point that it will become untenable for the attacker.
Secondly, there is the possibility of a validating node going rogue and validating malicious transactions. Another threat of the same nature can occur when there is a fork of the network. According to knowledgeable observers, it is possible for nodes to stake tokens on both sides of the forks such that they can undertake double transaction.
In mitigation, some developers are creating a hybrid of PoW and PoS whereby users cannot spend twice. Here, their tokens instantly become worthless once there is network fork. For instance, Ethereum is working on an improved version of PoS called “Casper” which will help to rein in such rogue validators.
Aspiring to make a lucrative career as a blockchain expert but not sure how? Check the detailed guide Now on How To Become A Blockchain Expert
Summary/Closing Comments
Blockchain technology is undergoing fundamental transformation as the need for tighter security and more decentralization bites. Further, the cost of mining is significantly high and has many enthusiasts dropping by the road side. Therefore, there is also need for the consensus algorithm to support cheaper and faster methods to guarantee the long term application of the technology.
The major consensus protocol that is popular today is proof of work. Notably, the algorithm powers bitcoin and Ethereum (before full migration to proof of stake). Particularly, the algorithm is still the favorite because of the Byzantine Fault Tolerance (BFT) characteristic. However, the energy intensive nature poses an existential threat.
The alternative consensus protocol is proof of stake where validators use their cryptocurrency as stake for them to participate in mining. In particular, the algorithm is energy and cost efficient and the validation process is fast. Below is a detailed comparison of the two algorithms.
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!