Learn how blockchain truly works, master key definitions, and uncover what makes smart contracts so "smart." Dive into the fundamentals, gain valuable insights, and start your blockchain journey today!
- Comparisons
Diego Geroni
- on August 23, 2021
Tokenization vs Encryption – Key Differences
Many years have passed since we first came across the phrase, ‘Data is the new lifeblood of businesses.’ However, the incidents of data breaches in recent years show that enterprises have not been successful in managing their most vital asset and their security. Transmission of data without any protective layer in the present times would lead to formidable security threats.
Even if encryption is a suitable approach for safeguarding sensitive information, it does not ensure comprehensive protection. As a result, enterprises have to turn towards additional security measures. Therefore, the tokenization vs encryption debate has become one of the focal points of attention for enterprises and tech enthusiasts.
Will this debate change the perception of security for enterprise systems and data? Will tokenization serve as a better alternative to encryption? Let us find answers to these questions by reflecting on differences between encryption and tokenization in the following discussion.
Want to learn the fundamentals of tokenization? Enroll Now: Tokenization Fundamentals Course
The Need for Comparison between Tokenization and Encryption
Tokenization and encryption are generally associated with each other frequently as the preferred choices for security of information in the course of its transmission on the internet or during its storage at rest. Interestingly, both of them help in addressing the data security policies of an organization while ensuring compliance with regulatory requirements. Some of the notable regulatory requirements, in this case, would include the PCI DSS, EU GDPR, HIPAA-HITECH, ITAR, and GLBA. The tokenization vs encryption comparison initially presents them as highly efficient technologies for data obfuscation.
However, it would be completely unreasonable to assume that both of them are the same thing. On the other hand, it is too quick to provide an answer for ‘is tokenization better than encryption?’ especially considering the fact that both the instruments have their strengths and weaknesses. So, either one of them could be a suitable method for securing data in different circumstances according to their strengths. Interestingly, both tokenization and encryption are implemented in certain cases for securing the end-to-end process, such as in the case of electronic payment data. Before outlining the differences between tokenization and encryption, let us understand each term comprehensively.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
Definition of Tokenization
Tokenization is basically the process of transforming meaningful data into a random string of letters, numbers, and characters. In the world of blockchain, tokenization focuses on transforming a real-world asset into a digital token. The token does not provide any value for malicious actors when it goes through a breach.
As a matter of fact, tokens would serve as references or pointers to the original data without any possibility for guessing the original values or data. One of the important factors in tokenization vs encryption is that tokenization does not leverage a mathematical process for transforming sensitive information into tokens.
You would not find any key or algorithm for deriving the original data associated with a token. On the contrary, tokenization leverages a database, generally referred to as a token vault. The token vault is responsible for storing the relationship between the token and the sensitive value it represents.
At the same time, the real data in the vault is subjected to encryption. It is possible to use the token value as a replacement for the real data in different applications. Users must submit the token to the vault, and then the index helps in obtaining the real data required in verification processes.
-
Value of Tokenization
One of the foremost value advantages associated with tokenization is that the end-user doesn’t have to go through complex processes. On the contrary, the browser or application of the end-user helps in retrieving real data instantly while storing transaction data on the cloud in different formats.
The tokenization vs encryption debate also turns in favor of tokenization due to the mathematical connection between tokens and real data. So, tokenization ensures security for the real value of the data rather than securing the data itself.
Even if an agent is successful in gaining access to a token, they cannot use it to derive useful data. It is practically impossible to use a key for reversing tokens to their original values. For instance, a token could store the last four digits in a credit card number for printing the tokenized number on the customer receipt.
As a result, the customer could see the reference to the actual credit card number. The printed characters on the receipt would include asterisks only, except the last four digits. Therefore, the merchant could not get the real card number, and they only get a token for security considerations.
Want to understand the critical data privacy issues for blockchain solutions? Enroll in the Blockchain And Data Privacy Masterclass now!
Definition of Encryption
If you want to find the answer to ‘is tokenization better than encryption?’ you need to learn about encryption in detail for an effectively reliable comparison. Encryption refers to the process of leveraging an algorithm for transformation of information in plain text to an unreadable format referred to as ciphertext.
The process of encryption depends profoundly on algorithms and encryption keys. The algorithm and encryption key is essential for obtaining the original value from encrypted information. The most commonly implemented form of encryption in present times refers to SSL encryption, which safeguards information during transmission on the internet.
-
Types of Encryption
Many people all over the world use in-built encryption features in operating systems and third-party encryption tools for safeguarding their sensitive data against concerns of accidental loss. Furthermore, encryption also finds promising applications in warding off concerns of government surveillance and theft of sensitive enterprise data. The two common approaches for implementing encryption refer to symmetric key encryption and asymmetric key encryption.
Symmetric key encryption is same as the approach of using a key for unlocking and locking the door for a house. However, the symmetric key encryption approach comes with certain setbacks. For example, a compromised key could help in unlocking the data it had helped in securing. Therefore, the asymmetric key encryption approach evolved for enabling multiple parties to engage in exchanges of encrypted data without management of similar encryption keys.
In the case of asymmetric key encryption, you can find two distinct keys for encryption and decryption processes. The public key is useful only for locking the data and can be distributed freely as it does not unlock data. For instance, a merchant could encrypt payment data with a public key before sending it to a payment processing provider. The payment processing provider will use the private key for decrypting the payment data and processing the payment. Asymmetric key encryption also serves as a useful tool for validating identity on the internet by leveraging SSL certificates.
Want to know the difference between private key & public key and how they work? Check out this ultimate guide on Private Key Vs Public Key now!
-
Is Tokenization better than Encryption?
Well, you have been searching for answers to this question throughout this discussion now. As a matter of fact, encryption users have to worry a lot about the keys to ensure safety of their sensitive information. For example, regular rotation of keys is essential for reducing the possibility of using a compromised key for decryption of all important data.
On the other hand, rotation of keys can restrict the amount of data that can be encrypted with a single key. So, data encrypted with a specific key would be minimum, and in event of a compromised encryption key, you would lose only a trivial amount of data. Another prominent setback associated with encryption refers to breaks in application functionality. As a matter of fact, reflecting on the tokenization vs encryption debate would show that data encryption in applications could affect features such as searching and sorting.
Since ciphertext is different from original data, it could also disrupt field validation if an application needs particular formats in fields like email addresses or payment card numbers. However, new encryption schemes with order-preserving, searchable, and format-preserving traits could enable better safeguards for information without compromising user functionality. On the other hand, the new encryption schemes often come with the need for a tradeoff between strength of encryption and the functionality of application.
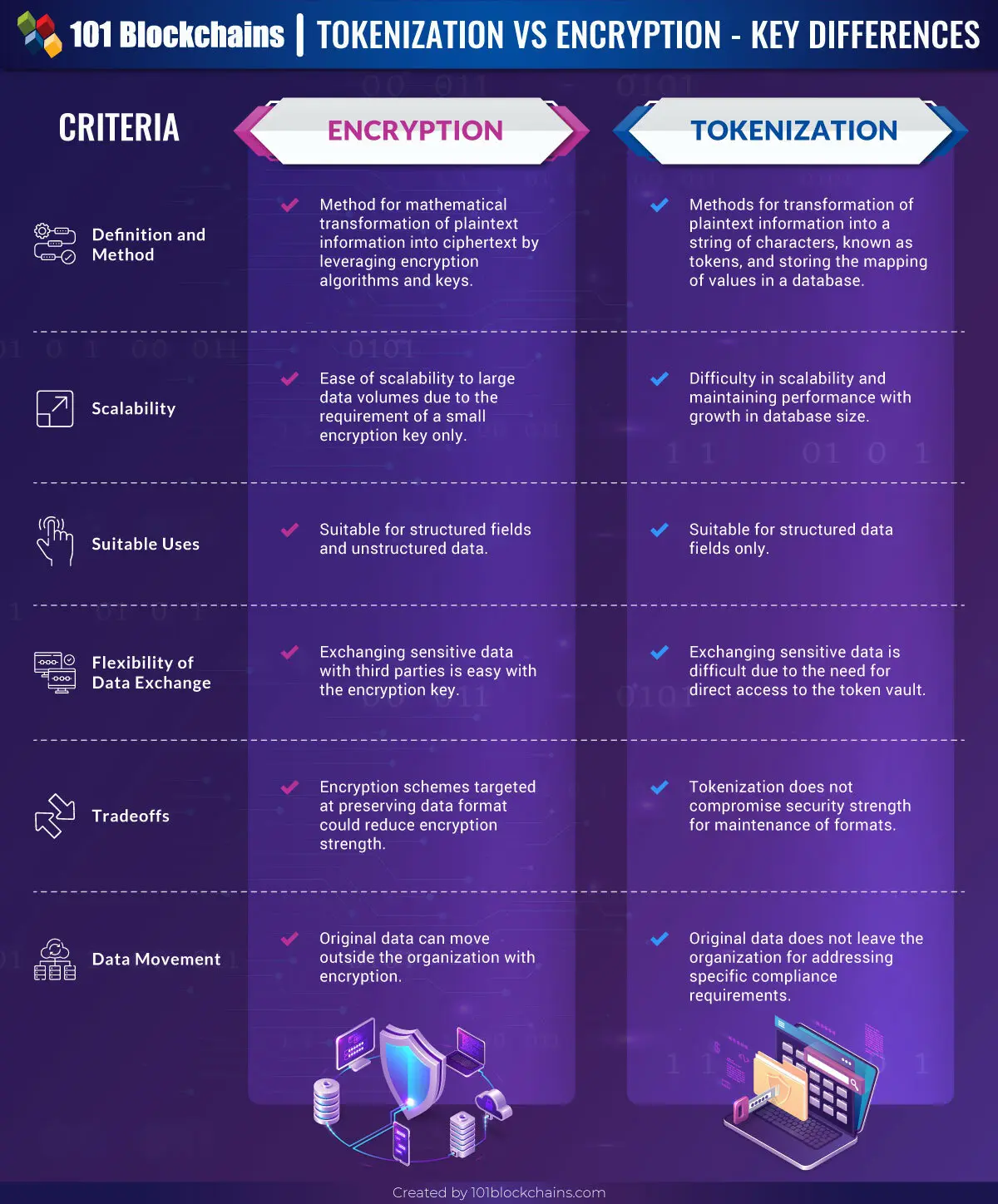
Difference between Tokenization and Encryption
Please include attribution to 101blockchains.com with this graphic. <a https://101blockchains.com/wp-content/uploads/2021/08/Tokenization-vs-Encryption-Key-Differences-1.jpg' alt='Tokenization vs Encryption='0' /> </a>
The basic understanding of both encryption and tokenization could not be adequate for finding an answer to ‘is tokenization better than encryption?’ and you would have to focus on other points of difference. Let us take a look at the differences between tokenization and encryption in detail on the grounds of following factors.
-
Definition and Method
Tokenization and encryption are just methods utilized for security of sensitive information or data transmitted through the internet. Tokenization replaces sensitive data with a completely unrelated random value known as tokens. On the other hand, encryption focuses on transforming plaintext information into ciphertext by leveraging encryption algorithms and keys.
Tokenization helps in creating two different databases, one for storing the actual data and the other for storing tokens correlated with every piece of the real data. So, it basically creates a token for plaintext information and stores the mapping of the token to its real value on another database. Encryption scrambles plaintext information, although with possibilities of reversing encryption by using the right key.
-
Scalability
The use of tokenization vs encryption in modern applications for data security also brings scalability into consideration. With continuously changing trends in the modern business environment, enterprises have to be prepared for anything. One of the most important concerns for an enterprise refers to the creation of additional data with passing the time. Encryption can provide support for scalability to large data volumes by using only the encryption key. On the contrary, tokenization presents considerable difficulties in secure scalability and maintaining performance levels with increasing database sizes.
Are you into blockchain technology and still wondering what the relation between blockchain and database is? Here’s a guide to finding the comparison between Blockchain vs Database.
-
Suitable Uses
The suitable areas of application also shed adequate light on the differences between tokenization and encryption. Encryption is suitable for structured fields as well as unstructured data, such as complete files in their entirety. However, tokenization is only suitable for use in structured data fields. Tokenization focuses on structured data fields such as social security numbers or payment card numbers.
-
Flexibility of Data Exchange
The answer to ‘is tokenization better than encryption?’ would also focus on the ease of data exchange with both tools. Encryption is a reliable option for exchange of confidential data with third parties having the encryption key. On the other hand, tokenization needs direct access to the token vault, which maps token values for facilitating data exchange. Therefore, tokenization presents formidable difficulties for exchanging sensitive data.
-
Tradeoffs
Another noticeable factor that you should take into account in the tokenization vs encryption debate refers to the tradeoffs associated with them. Tradeoffs refer to the things you have to give up in order to get the benefit of security. In the case of encryption, you will come across the dilemma of preserving data format or retaining encryption strength.
As a matter of fact, some encryption schemes with format-preserving capabilities come with the tradeoff of lower encryption strength. Tokenization presents a formidable advantage in this case as it could ensure maintenance of the format without compromising security strength.
-
Data Movement
The final aspect of difference in the tokenization vs encryption comparison would refer to the scope for movement of data. In the case of encryption, the original data could leave the organization, albeit in encrypted form. On the other hand, tokenization does not allow the original data to leave the organization for addressing specific compliance requirements.
Curious to learn about blockchain implementation and strategy for managing your blockchain projects? Enroll Now in Blockchain Technology – Implementation And Strategy Course!
Final Words
Based on an overview of the differences in the tokenization vs encryption debate, it is reasonable to assume that each of them is rightfully useful. However, the choice of tokenization or encryption as a better alternative depends considerably on the use case in question. For example, if you have limited compliance requirements and large volumes of unstructured data, encryption might be the best pick.
On the other hand, tokenization could be useful in cases involving strict compliance requirements and structured data. Therefore, it is clear that the choice between encryption and tokenization is not easy. Learn more about tokenization and how it can transform the management of information and assets!
*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!